Author: Cybernoz
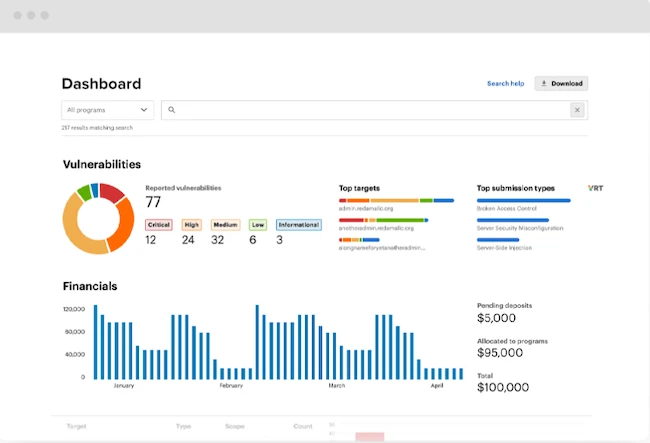
Bugcrowd’s new service connects customers with a global network of vetted ethical hackers for a variety of red team engagements—fully…
Your iPhone isn’t necessarily as invulnerable to security threats as you may think. Here are the key dangers to watch…
Microsoft announced that hotpatching support for Windows Server 2025 will become generally available as a subscription service starting July 1,…
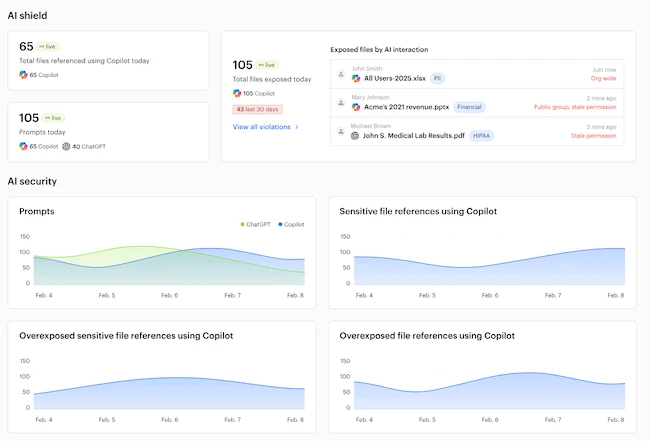
Varonis announced always-on AI risk defense that continuously identifies data exposure in real time, flags violations, and automatically fixes issues…
Veeam is all set to fully launch version 13 of its Veeam Data Platform (VDP) – the platform upon which…
Law enforcement agencies from the UK and the Netherlands have dismantled the notorious JokerOTP cybercrime platform, which is allegedly linked…
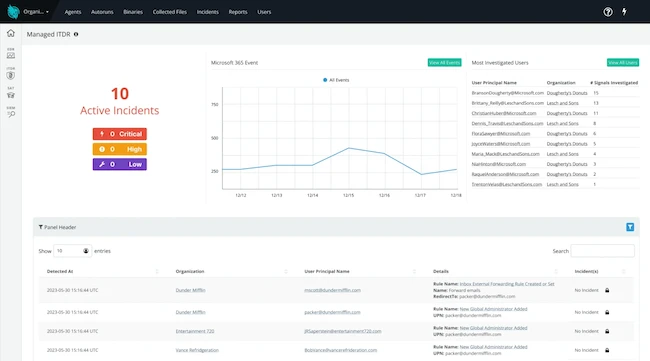
Huntress has unveiled its newly enhanced Managed Identity Threat Detection and Response (ITDR) solution, purpose-built to wreck hacker identity tradecraft,…
Thank you for joining! Access your Pro+ Content below. 29 April 2025 Making divorce digital Share this item with your…
In an engaging video podcast with Mihir Bagwe of The Cyber Express, Kapil Yewale, Head of Cybersecurity at Clearview, shared…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert concerning a newly disclosed security flaw in…
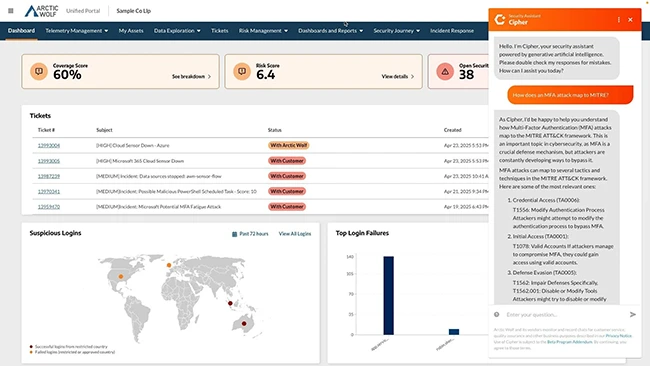
Arctic Wolf has introduced Cipher, an AI security assistant that provides customers with self-guided access to deeper security insights directly…
U.S. CISA adds Qualitia Active! Mail, Broadcom Brocade Fabric OS, and Commvault Web Server flaws to its Known Exploited Vulnerabilities…