Author: Cybernoz
In this Help Net Security interview, Christopher Kennedy, CISO at Group 1001, discusses how cybersecurity initiatives are reshaping enterprise cybersecurity…
Apr 29, 2025Ravie LakshmananVulnerability / Web Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two high-severity…
SA Health has notified patients involved in sleep studies at the Adelaide Women’s and Children’s Hospital that some of their…
Analyst IV – Cybersecurity Carpenter Technology | USA | On-site – View job details As an Analyst IV – Cybersecurity,…
Iran repelled a large cyberattack on its infrastructure on Sunday, said the head of its Infrastructure Communications Company, a day…
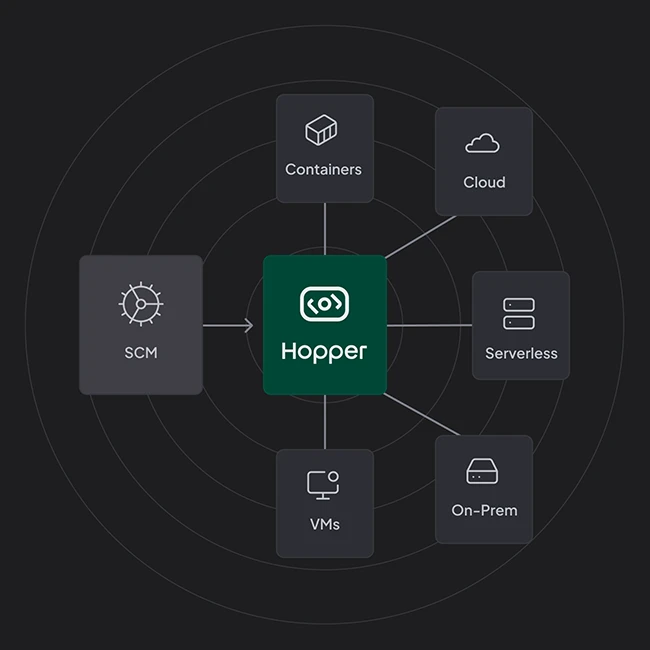
Modern software relies on open-source. As open-source software (OSS) scaled, accelerated by AI, legacy security tools failed to keep pace,…
Chinese artificial intelligence service DeepSeek became available again on South Korean app markets this week for the first time in…
Commvault has announced an expanded partnership with CrowdStrike. Through this expanded partnership, the two companies will deliver coordinated cyber recovery…
Bapcor, home to automotive brands such as Autobarn and Midas, is cutting dozens of enterprise resource planning (ERP) systems from…
Postal codes now play a key role in cybersecurity, fraud prevention, and digital identity verification, raising new concerns over privacy…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
New research from ISACA reveals despite mounting concern among 62% of technology and cybersecurity professionals that quantum computing could shatter…