Author: Cybernoz
Two significant security vulnerabilities in generative AI systems have been discovered, allowing attackers to bypass safety protocols and extract potentially…
As we navigate 2025, Chief Information Security Officers (CISOs) must prepare for the Top 5 Cybersecurity Risks emerging from a…
Despite significant disruptions by international law enforcement operations targeting major ransomware schemes, cybercriminal groups continue demonstrating remarkable adaptability in 2025….
In the world of cybersecurity, we’ve all encountered those articles: lists that tell us the top ten metrics to track to…
The cybersecurity landscape faces an escalating crisis as AgeoStealer joins the ranks of advanced infostealers targeting global gaming communities. Documented…
Immersive security researchers discovered critical vulnerabilities in Planet Technology network management and switch products, allowing full device control. Learn about…
A sophisticated phishing campaign dubbed “Power Parasites” has been actively targeting global energy giants and major brands since 2024, according…
Extended Detection and Response (XDR) has emerged as a transformative security technology that unifies visibility across multiple security layers. When…
In the ever-evolving world of cybersecurity, organizations must continuously adapt their defense strategies to stay ahead of increasingly sophisticated threats….
A critical vulnerability (CVE-2025-31324) in SAP NetWeaver Visual Composer puts systems at risk of full compromise. Learn how to check…
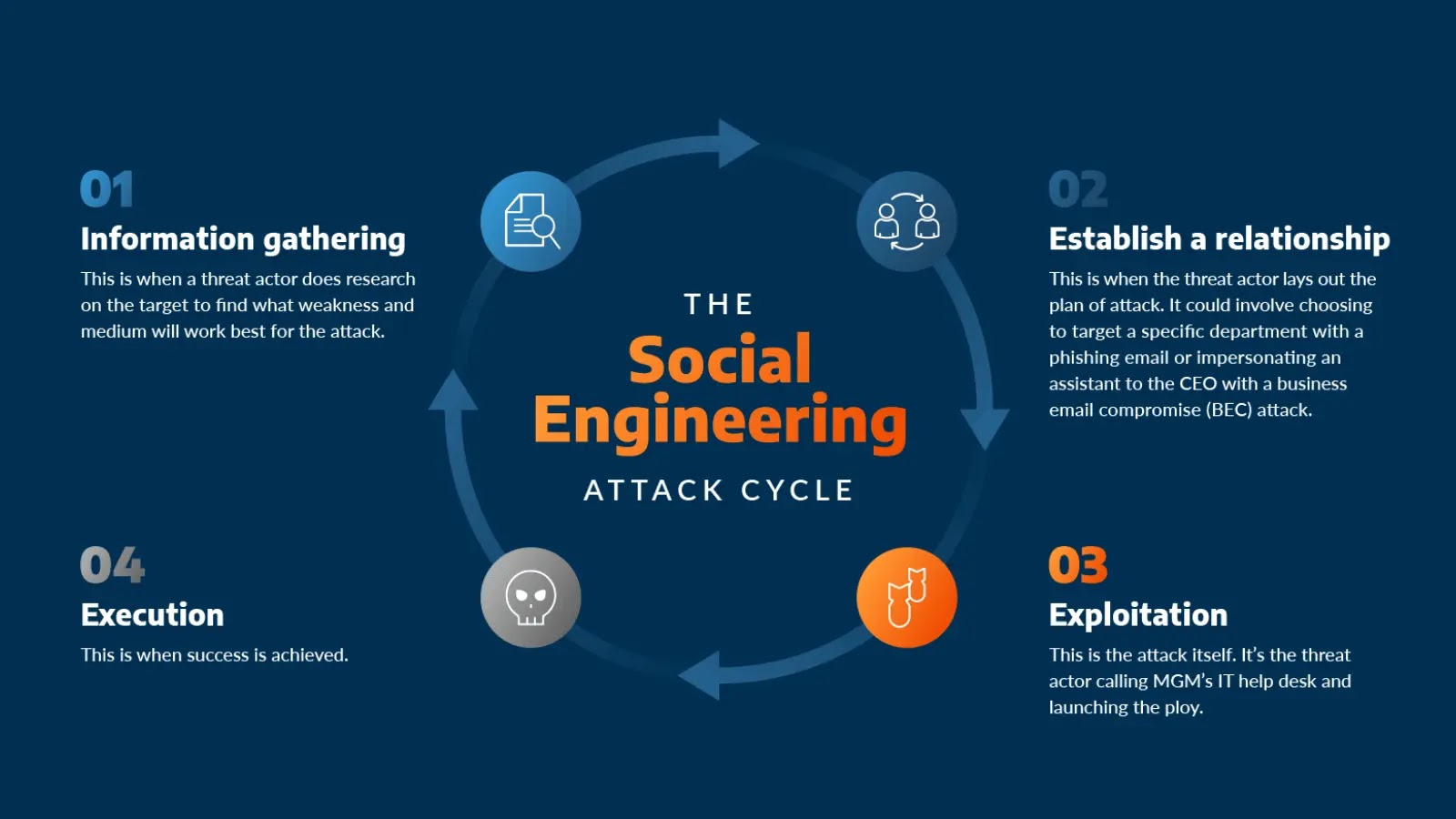
Social engineering has become the dominant attack vector in the modern cybersecurity landscape. As technical defenses evolve and strengthen, attackers…
The cybersecurity landscape has changed dramatically in recent years, largely due to the introduction of comprehensive data protection regulations across…