Author: Cybernoz
A serious vulnerability related to information exposure (CVE-2025-22234) impacts several versions of the spring-security-crypto package. The flaw enables attackers to…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
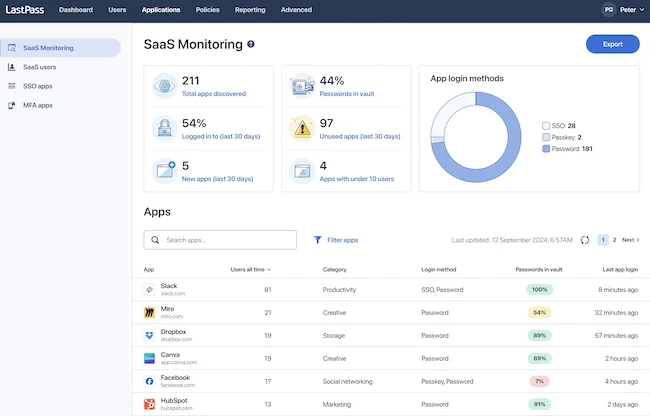
As cloud app adoption continues to rise, and the modern workplace continues to evolve, LastPass will introduce a new approach…
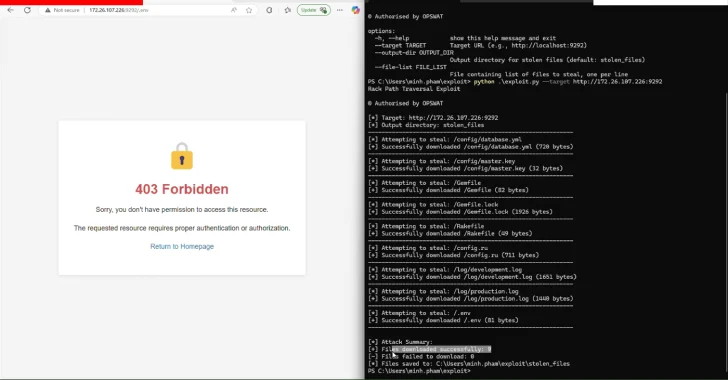
Apr 25, 2025Ravie LakshmananVulnerability / Data Breach Cybersecurity researchers have disclosed three security flaws in the Rack Ruby web server…
A recent Microsoft security update, intended to patch a critical privilege escalation vulnerability, has inadvertently introduced a new and significant…
VulnCheck’s latest report for Q1 2025 has identified 159 Common Vulnerabilities and Exposures (CVEs) publicly disclosed as exploited in the…
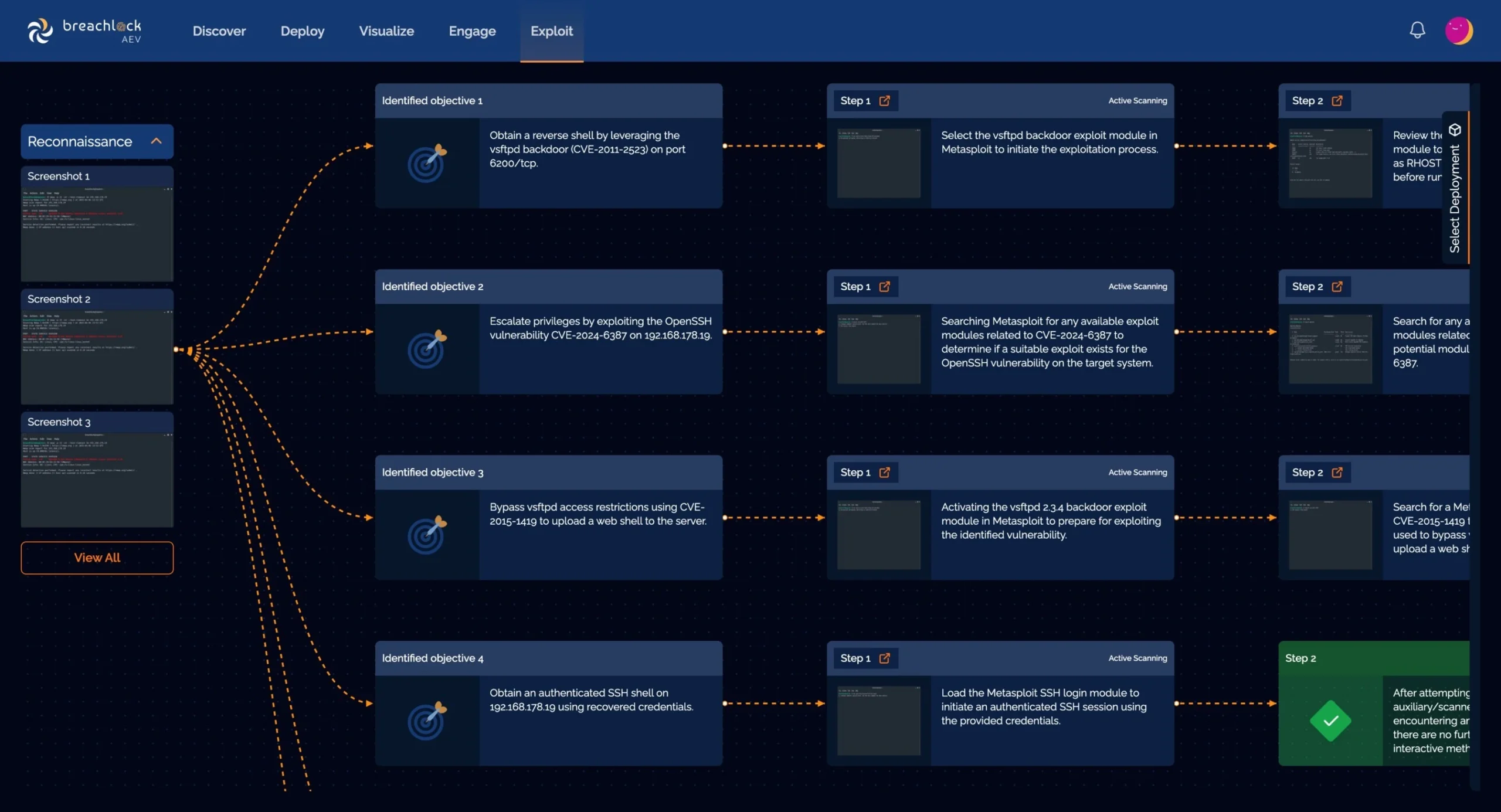
BreachLock AEV automates multistep, threat-intelligence-led attack scenarios—helping security teams uncover real exposures and prioritize what matters most. Going beyond just…
Microsoft says it will soon fix a known issue causing CPU spikes when typing messages in recent versions of its…
Trend Research has uncovered a sophisticated network of cybercrime operations linked to North Korea, heavily utilizing Russian internet infrastructure. Specifically,…
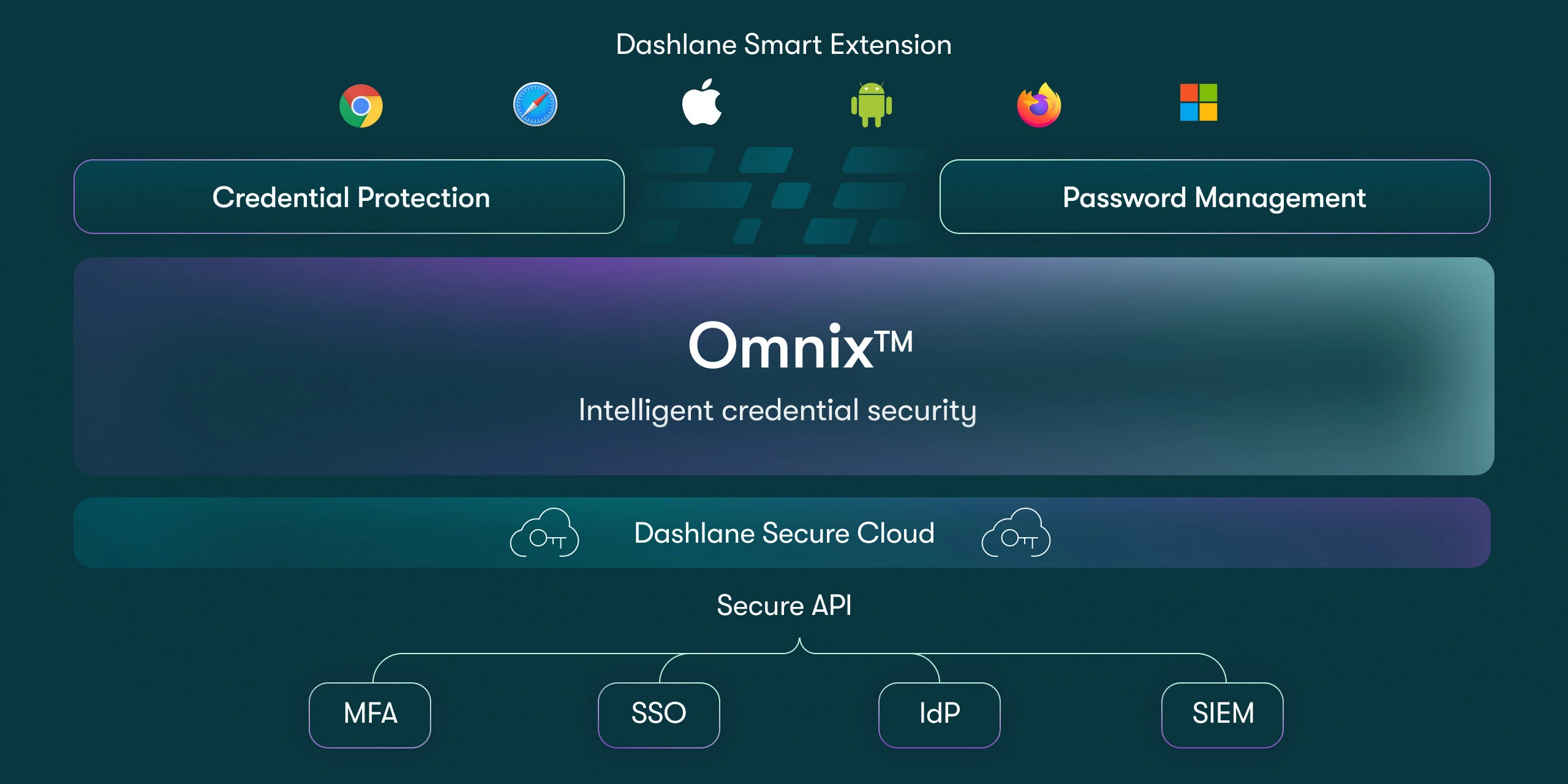
Dashlane unveiled a new approach to addressing human risk in response to the rise of AI-driven phishing attacks and shadow…
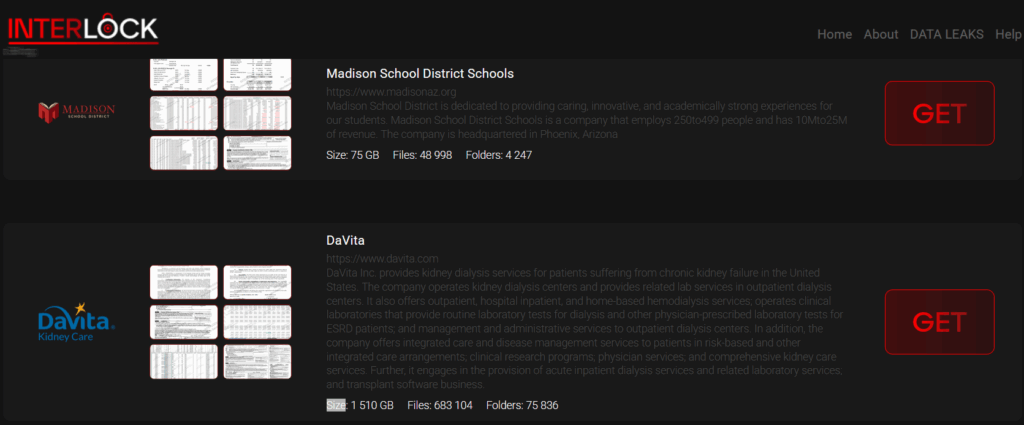
Interlock ransomware gang started leaking data allegedly stolen from leading kidney dialysis firm DaVita Pierluigi Paganini April 25, 2025 The…
A newly identified security vulnerability, CVE-2025-22234, has exposed a critical weakness in the widely-used Spring Security framework. According to the…