Author: Cybernoz
Developing an engineering project is a challenge by itself. In the practice, dealing with some product or service is very…
A new Android malware has been discovered hidden inside trojanized versions of the Alpine Quest mapping app, which is reportedly used…
Significant vulnerabilities in popular browser-based cryptocurrency wallets enable attackers to steal funds without any user interaction or approval. These critical…
Apr 23, 2025Ravie LakshmananMalware / Cryptocurrency Multiple threat activity clusters with ties to North Korea (aka Democratic People’s Republic of…
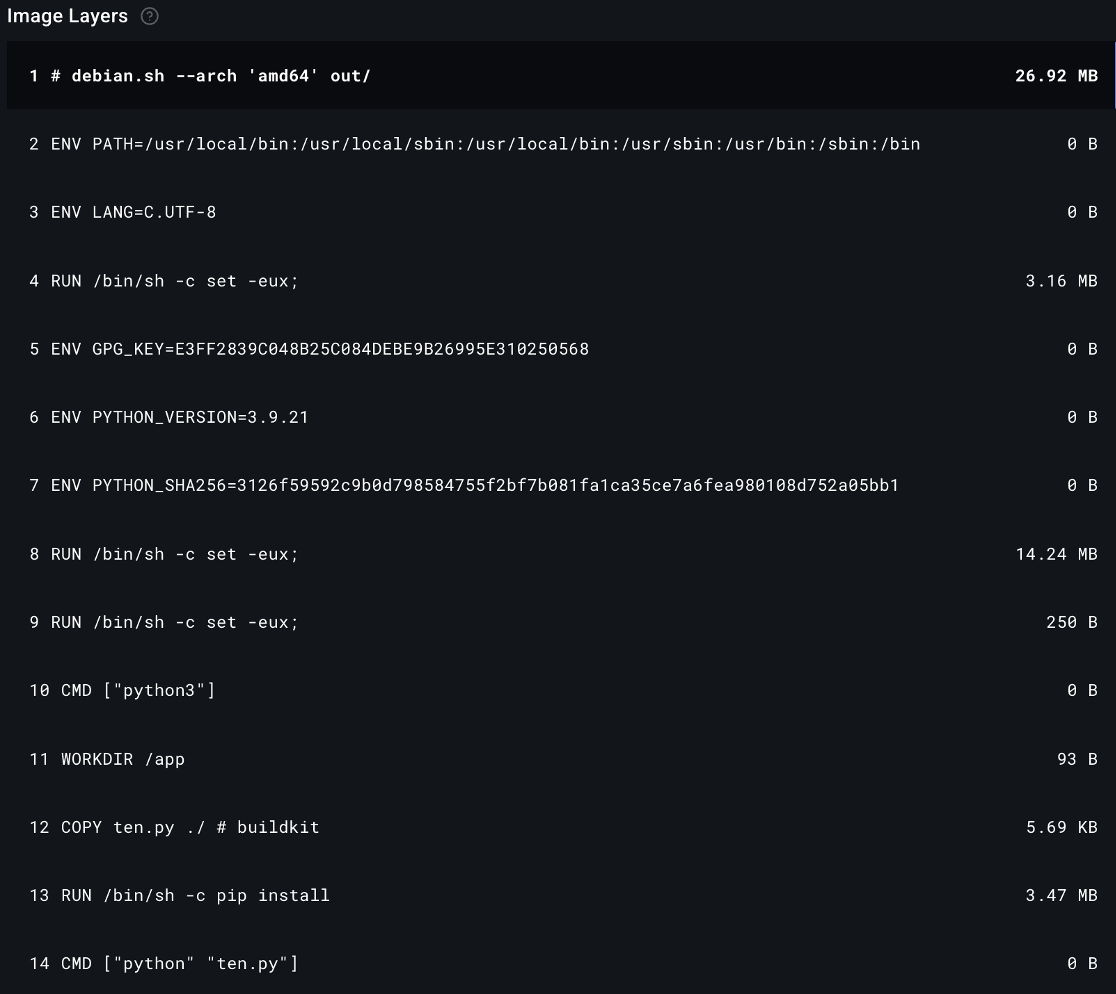
Crypto mining campaign targets Docker environments with new evasion technique Pierluigi Paganini April 23, 2025 New malware campaign targets Docker…
It looks like 2024 was a record year in cybercrime for all the wrong reasons, according to the FBI’s annual…
WhatsApp has introduced a new Advanced Chat Privacy feature to protect sensitive information exchanged in private chats and group conversations….
A severe security vulnerability in Synology’s DiskStation Manager (DSM) software has been identified. This vulnerability allows remote attackers to read…
Cybersecurity firm Volexity has tracked a series of highly targeted attacks by suspected Russian threat actors, identified as UTA0352 and…
The Trump administration’s plan to overhaul the State Department for the modern era could halt the U.S.’s recent progress on…
Phishing attacks remain a huge challenge for organizations in 2025. In fact, with attackers increasingly leveraging identity-based techniques over software…
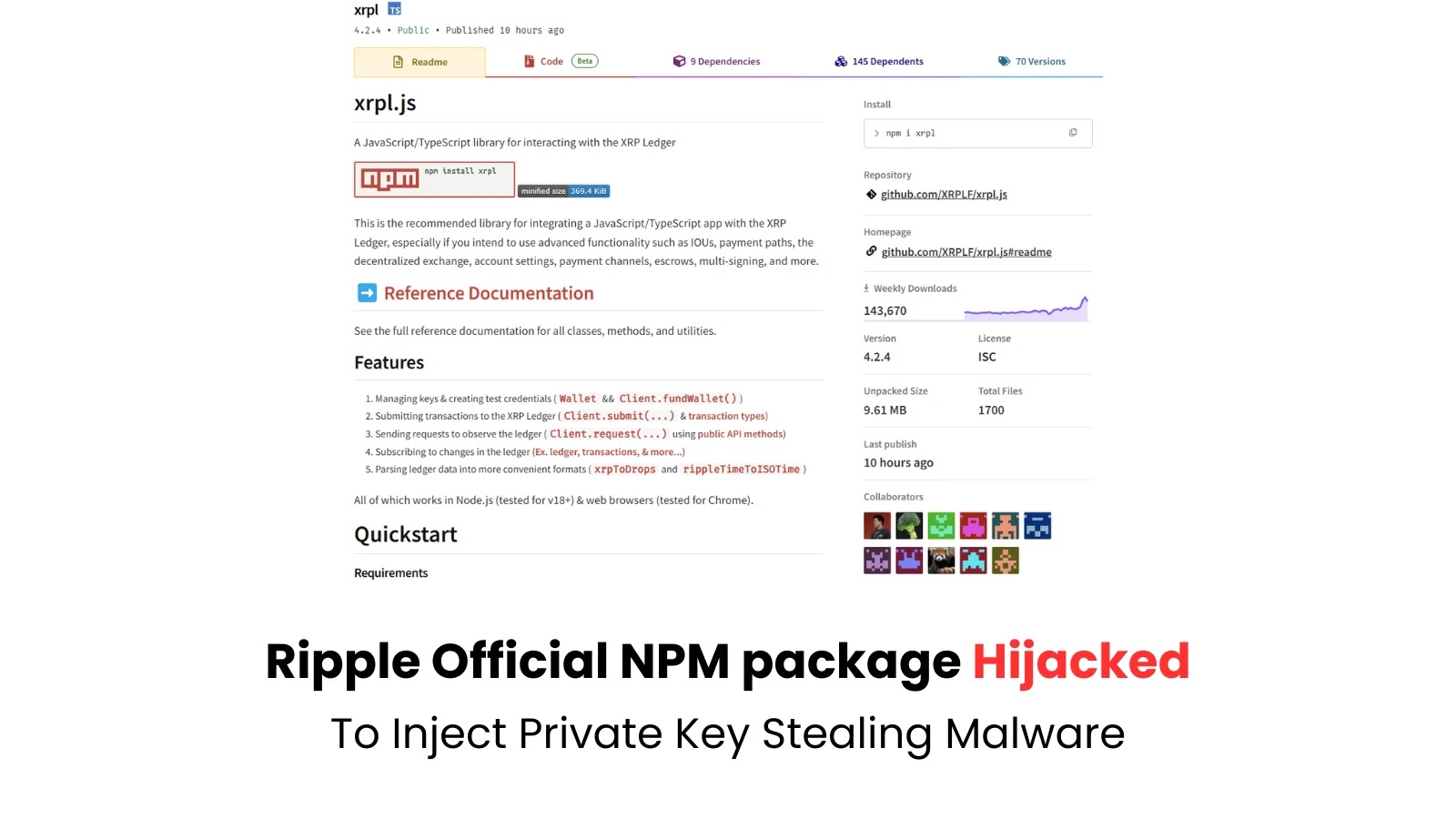
A significant supply chain attack targeting cryptocurrency users. The official XRPL (Ripple) NPM package, which serves as the JavaScript SDK…