Author: Cybernoz
I have a number of friends who actually post insightful ideas and comments on Facebook, and they do so semi-regularly….
Microsoft has fixed several known issues that caused Blue Screen of Death (BSOD) and installation issues on Windows Server 2025…
Leading British retailer Marks & Spencer Group plc (M&S) has confirmed it has been grappling with a cyberattack over the…
On April 21, 2025, British retail giant Mark and Spencer (M&S) confirmed that it was the victim of a cyberattack…
Application Security Analyst Greenway Health | India | Remote – View job details As an Application Security Analyst, you will…
I think a lot about creativity and how to maximize it, and one of my latest ideas has been to…
In this increasingly digital world, cybersecurity has become more than just an IT concern; it’s a critical aspect of every…
Skyhawk Security expanded its AI-powered Autonomous Purple Team to include custom cloud applications. For the first time, organizations can preemptively…
I often challenge people to describe why their lives have meaning. In most cases, the answers are deeply unsatisfying, both…
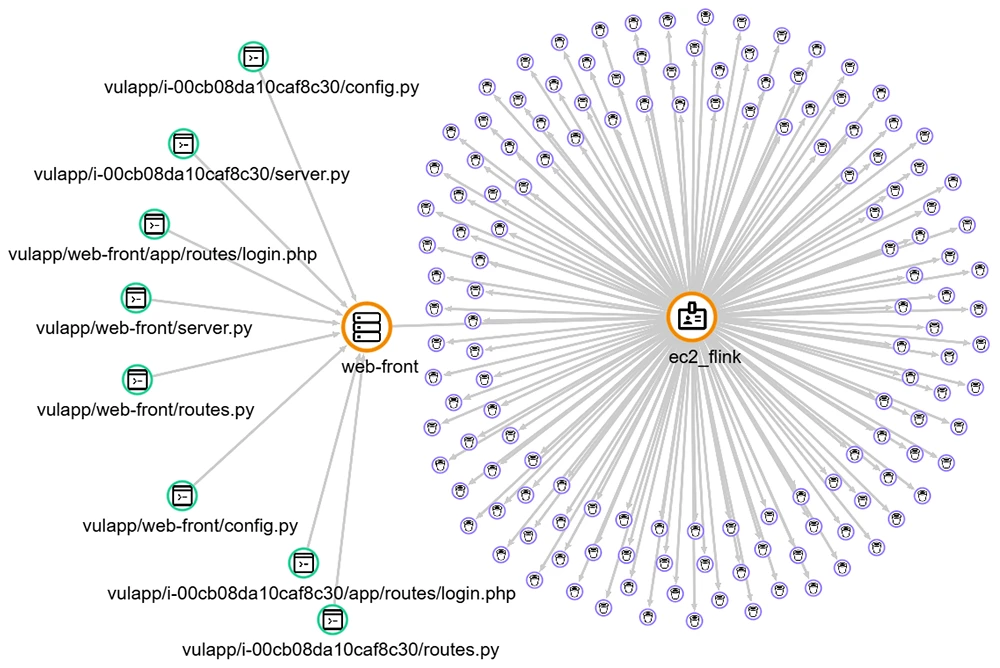
A critical privilege-escalation vulnerability in Google Cloud Platform (GCP), dubbed “ConfusedComposer,” could have allowed attackers to gain elevated permissions to…
In 2005, cell phones were banned for the first time during the conclave, the process by which the Catholic Church…
Research disclosed a now-patched high-severity vulnerability in Google Cloud Platform’s (GCP) Cloud Composer service, dubbed ConfusedComposer. It could have allowed attackers…