Author: Cybernoz
Artificial intelligence is transforming industries, but its adoption also raises ethical and cybersecurity concerns, especially in the regulated financial sector….
Telco regulator Ofcom has said it is closing a technical loophole that poses a risk to mobile users’ privacy and…
If you’ve ever had a problem deleting a horizontal line in Microsoft Word, this post is for you. The answer…
Cybersecurity in Japan has hit a new low as the Financial Services Agency (FSA) reports a staggering increase in unauthorized…
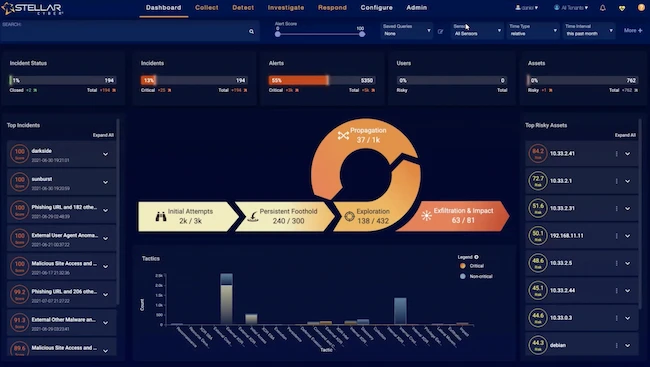
At the upcoming RSAC 2025 Conference in San Francisco, Stellar Cyber will unveil the next evolution of modern SecOps: the…
More than 150 billion application programming interface (API) attacks were observed in the wild during 2023 and 2024, according to…
There are many ways to explain SQL Injection, and the “best” way is clearly determined by who you’re talking to….
U.S. ports are vital to the flow of imports and exports; however, the entire maritime transportation system’s cybersecurity is exceedingly…
The Cybersecurity and Infrastructure Security Agency (CISA) has alerted its threat hunting teams to immediately discontinue use of two widely…
Abilene city, Texas, takes systems offline following a cyberattack Pierluigi Paganini April 22, 2025 Abilene, Texas, shut down systems after…
Like many others, I’ve been in a number of debates about gun control in recent weeks. Here are my main…
A newly discovered vulnerability in the Windows Update Stack, tracked as CVE-2025-21204, has sent shockwaves through the cybersecurity community after…