Author: Cybernoz
Cybersecurity threats are an ever-present danger in today’s interconnected world, and one of the most insidious types of breaches involves…
In this Help Net Security interview, Full Professor at University of Leuven, unpacks the European Commission’s encryption agenda, urging a…
A recent cyberattack on Marks and Spencer (M&S) has raised significant concerns, revealing that hackers infiltrated the UK-based retailer’s systems…
AI systems can sometimes produce outputs that are incorrect or misleading, a phenomenon known as hallucinations. These errors can range…
Coinbase, one of the largest cryptocurrency exchanges, has disclosed a significant data breach that exposed sensitive customer information, including government-issued…
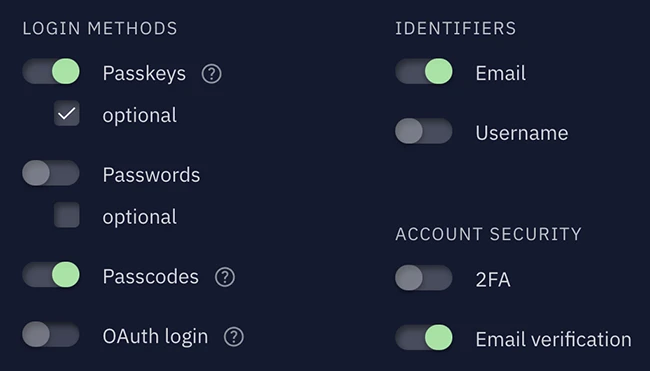
Hanko is an open-source, API-first authentication solution purpose-built for the passwordless era. “We focus on helping developers and organizations modernize…
The recent Twitter data leak, which exposed the personal information of 2.8 billion users, serves as a stark reminder of…
A critical vulnerability in Microsoft’s Remote Desktop Gateway (RD Gateway) that could allow attackers to execute malicious code on affected…
Riverina Water has revamped its asset management, finance and billing portals as part of a $4.5 million digital transformation, leading…
Bendigo and Adelaide Bank will switch on chargeback for internal departments using Kafka resources from July, but is already realising…
TPG Telecom-owned Vodafone has reported Telstra to Australia’s competition watchdog and is “considering” legal action over mobile coverage claims. The…
Microsoft has offered to make its Office product without Teams cheaper than when sold with Teams, EU antitrust regulators said,…