Author: Cybernoz
Ukrainian President Volodymyr Zelenskyy has signed a sweeping cybersecurity bill aimed at bolstering the protection of state networks and critical…
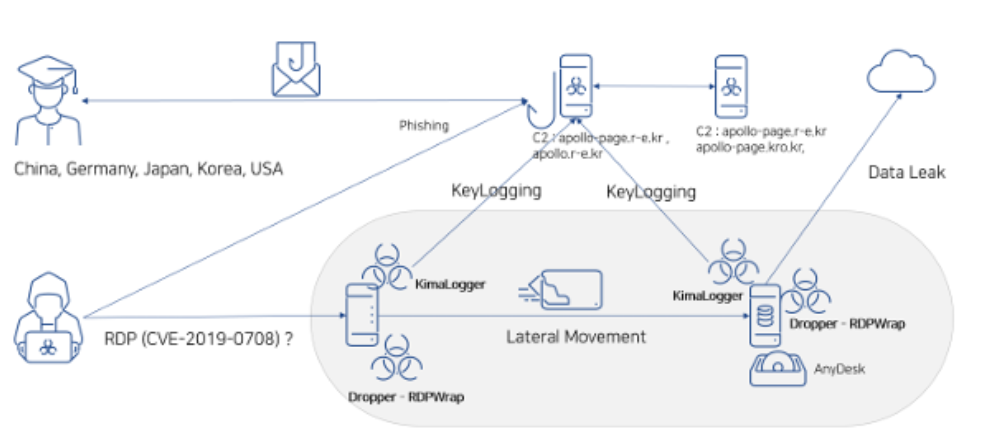
Kimsuky APT exploited BlueKeep RDP flaw in attacks against South Korea and Japan Pierluigi Paganini April 21, 2025 Researchers spotted…
Photo by Bill Hornstein When you’re inside of a mess it’s sometimes difficult to see it for what it is….
A federal judge last week placed strict limits on the kind of evidence NSO Group can raise during a trial…
Web-based attacks remain one of the most persistent threats to modern organizations, targeting everything from web applications and APIs to…
The volume of infostealer malware distributed through phishing emails has surged by 84% week-on-week in 2024, according to the latest…
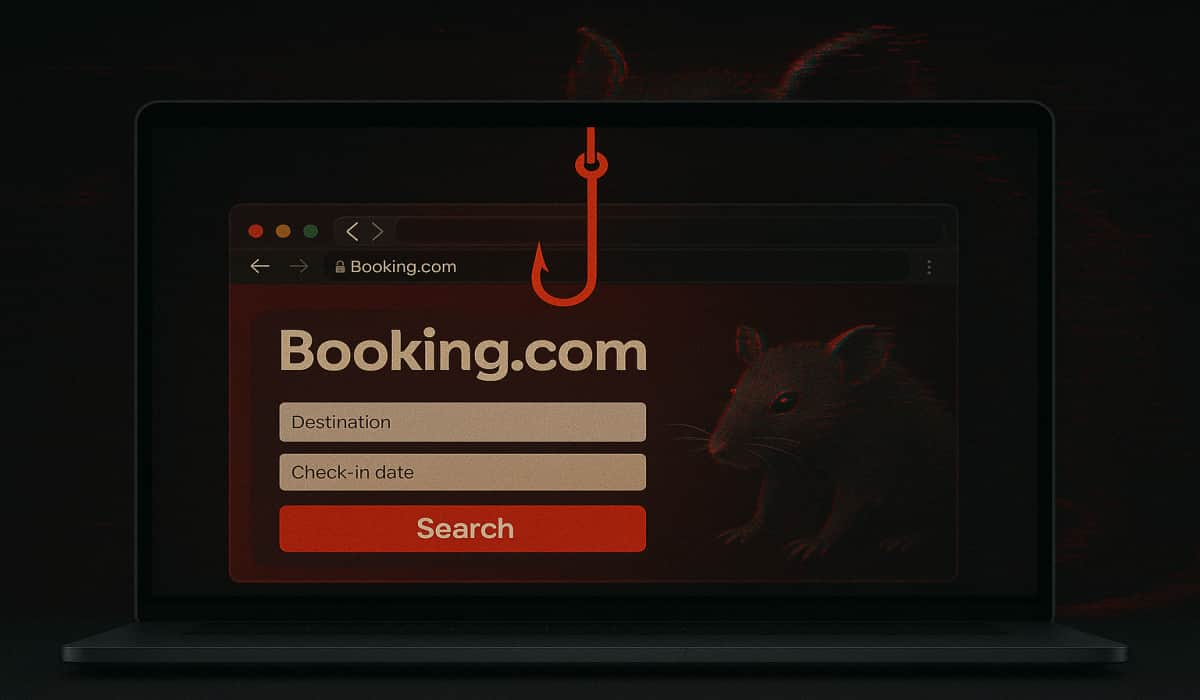
Fake Booking.com emails trick hotel staff into running AsyncRAT malware via fake CAPTCHA, targeting systems with remote access trojan. A…
November 12, 2012 I believe western civilization to be in the middle of a profound transition. The change I’m referring…
In 2025, digital forensics stands at the intersection of rapid technological innovation, increasingly sophisticated cyber threats, and the ever-expanding volume…
Cybersecurity experts have observed an alarming increase in the use of SVG (Scalable Vector Graphics) files for phishing attacks. These…
Apr 21, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored…
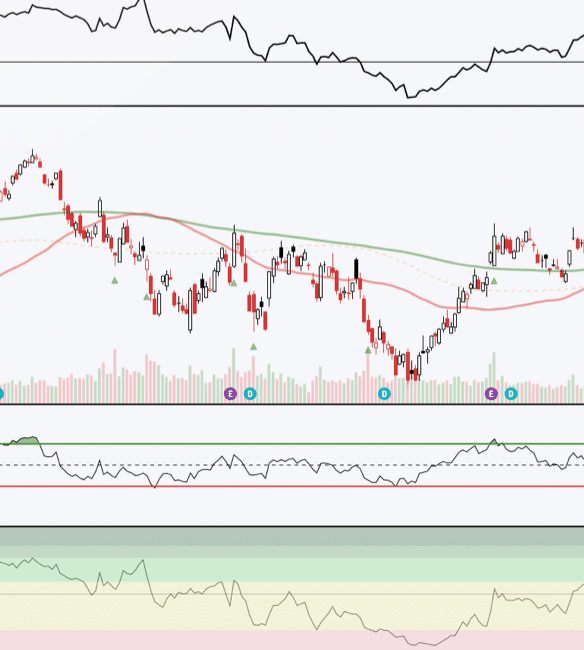
Japan’s Financial Services Agency (FSA) warned last week of the growing threat of hacked trading accounts that has resulted in…