Author: Cybernoz
Here’s a quality link for those who wish to know what Obama has done with his time in office. It’s…
A notorious threat actor has allegedly begun selling “Baldwin Killer,” a sophisticated malware toolkit designed to bypass leading antivirus (AV)…
You never really feel like you master it, but that’s not really the point. The point is to get intimate…
Privacy and digital rights advocates largely prefer the approach of building a travel device from scratch, but they caution that…
The Chinese hacker group known as Billbug, or Lotus Blossom, targeted high-profile organizations across Southeast Asia. The attackers, who were…
A major security flaw has been discovered in PyTorch, the widely used open-source machine learning framework. Identified as CVE-2025-32434, this…
Trickle-down economics, i.e. the idea that if you give the rich lots of money it will improve the economy, is…
Researchers have unveiled a sophisticated new technique that allows attackers to bypass traditional Antivirus (AV) and Endpoint Detection and Response…
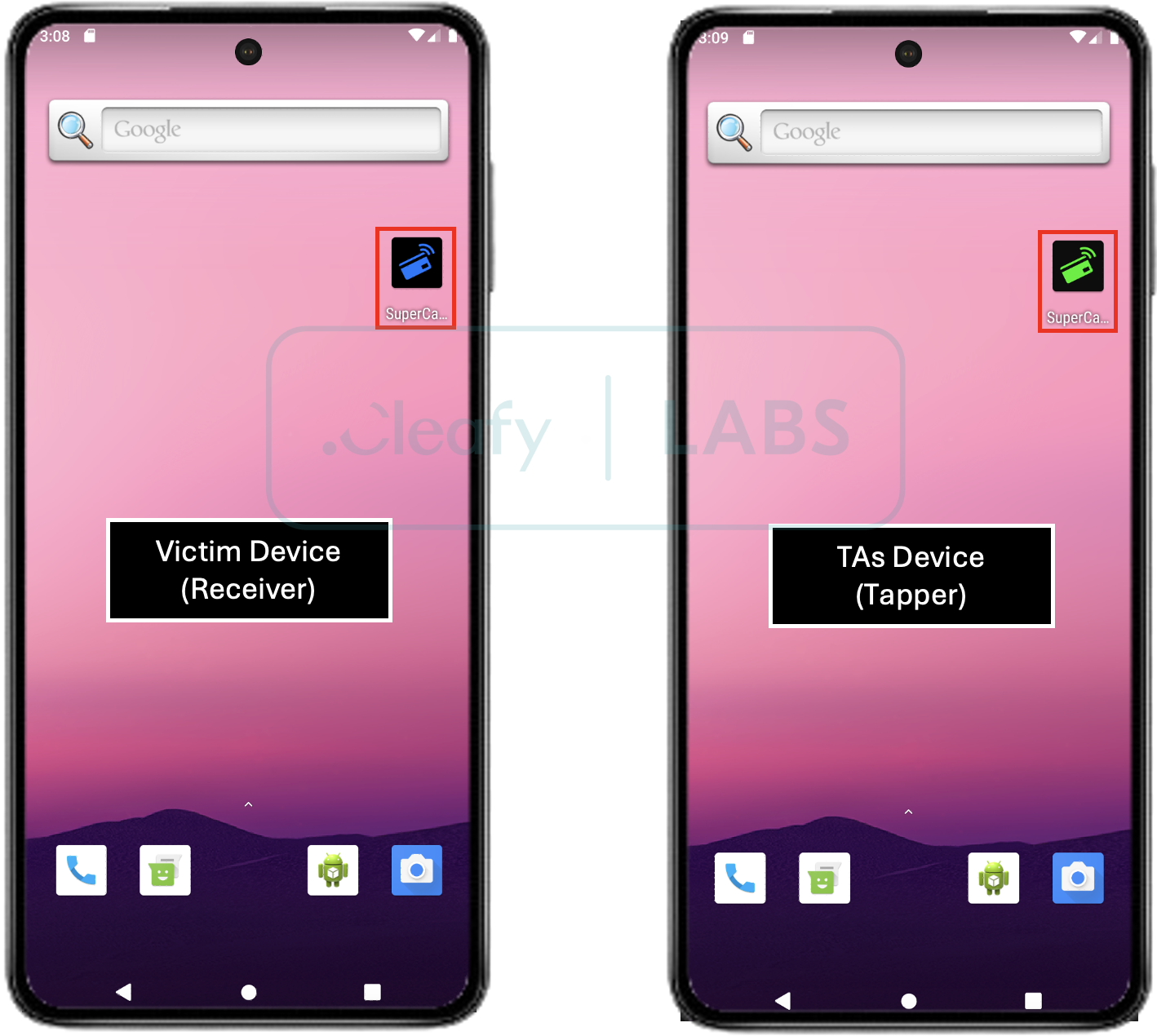
New sophisticate malware SuperCard X targets Androids via NFC relay attacks Pierluigi Paganini April 21, 2025 ‘SuperCard X’ – a…
When things are roughly similar, I value form over function. It’s that simple. Elegance, beauty, and design are all magnifiers…
The AhnLab SEcurity intelligence Center (ASEC) has released a detailed analysis of a sophisticated cyber campaign dubbed “Larva-24005,” linked to…
I just uninstalled TextMate. I also just revamped my git workflow, and am going full-on Vim everywhere. That’s MacVim, Janus,…