Author: Cybernoz
A sophisticated phishing attack exploiting a loophole in Google’s OAuth infrastructure has surfaced, raising significant concerns about the security of…
The ongoing trade dispute between China and the United States, commonly referred to as the “tariff war,” has created far-reaching…
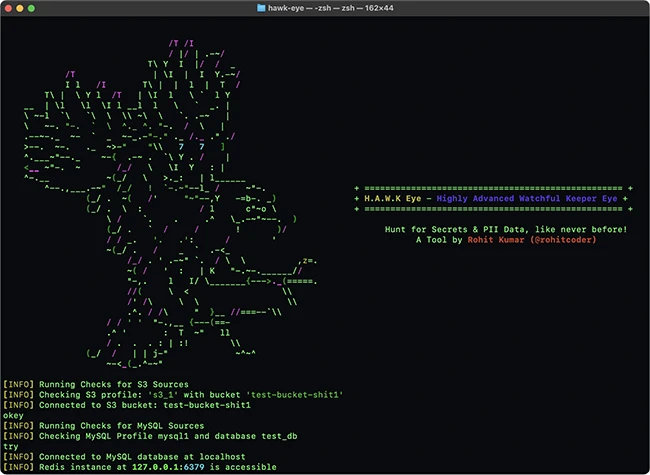
Hawk Eye is an open-source tool that helps find sensitive data before it leaks. It runs from the command line…
A high-severity vulnerability has been discovered in a range of industrial recorder and data acquisition systems produced by Yokogawa Electric…
Here’s what we should be saying to people who attack us, and to those who panic when we are attacked….
Attackers are focusing more on stealing identities. Because of this, companies need to use zero trust principles. They should also…
This video is an entertaining look at the hype and reality leading up to today’s iPhone 5 release. I think…
Businesses are losing out on an average of $98.5 million a year as a consequence of cyber threats, fraud, regulatory…
Hi $NAME, Basically, the role of the government is to provide for our welfare, to see that we flourish, etc….
It seems to me that every time I come across real philosophers they have an extremely pompous view of non-academic,…
I am demoing a Samsung Galaxy S III. It’s the new flagship Android device, and I like a lot about…
I’ve been thinking a lot recently about the habits of productive people. When I say productive I mean successful–as in…