Author: Cybernoz
Image by pshan427 In both health and information security it’s easy to become conceptually constrained by external advice, recommendations, and…
I feel like I cannot be the only one who is disgusted every time I walk through someones exhaled cigarette…
Security Affairs newsletter Round 520 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini April 20, 2025 A new round of…
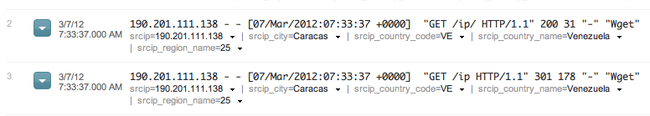
March 6, 2012 CloudFlare is a great service that proxies your site’s traffic in order to offer performance gains and…
Sam Harris’s book on free will came out today and I read it during dinner (it’s a short read). Here’s…
Before going into my qualms with Daniel Dennett’s capability/evitibility-based free will, I want to point out that most supporters of…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Apple plugs zero-day holes used…
When open allocation is in play, projects compete for engineers, and the result is better projects. When closed allocation is…
I think a lot about customer service. Or, what I really mean is that I get angry a lot about…
This is an essay about being productive to the world around you. Confused, you say, “How does any of that…
There’s some phenomenal password research here from clarkson.edu that talks about common passwords found during Internet attacks. I’ve taken those…
The Russian state-sponsored threat actor known as APT29 has been linked to an advanced phishing campaign that’s targeting diplomatic entities…