Author: Cybernoz
China has announced a significant step forward in its partnership with Russia, with plans to expand their cooperation in the…
Cyber security remained the most pressing challenge facing those in supply chain management roles during the first three months of…
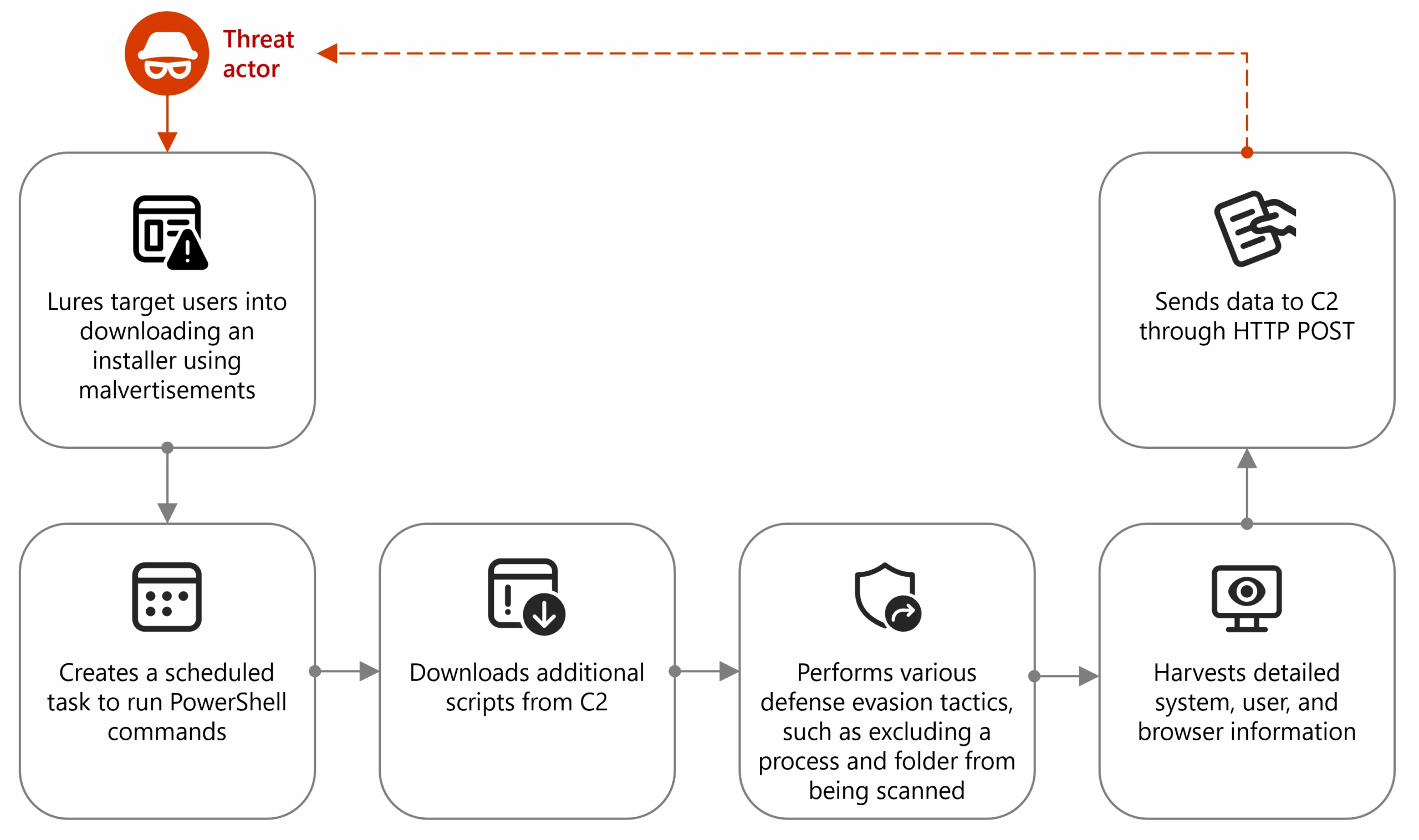
Node.js malvertising campaign targets crypto users Pierluigi Paganini April 17, 2025 Microsoft warns of a malvertising campaign using Node.js to…
So I got to see Sam Harris speak last night in Berkeley. It was stellar. A few things stood out:…
Microsoft has reminded customers that Office 2016 and Office 2019 will reach the end of extended support six months from…
A critical vulnerability in the widely adopted Model Context Protocol (MCP), an open standard for integrating generative AI (GenAI) tools…
Modern websites are under constant pressure from automated traffic: scraping, credential stuffing, inventory hoarding, and other malicious bot behaviors. While…
So my #1 issue in Table Tennis right now is getting angry, which results in a tightness that precludes the…
U.S. allies are among the 35 countries where mobile providers employ China-based networks for transporting user traffic, opening travelers and…
A new ransomware variant known as “Ghost” (also referred to as Cring) has emerged as a significant danger. Since its…
The global threat landscape is projected to become more sophisticated, with cybercrime expected to cost the world $10.5 trillion annually by…
CVE-2025-24054, a Windows NTLM hash disclosure vulnerability that Microsoft has issued patches for last month, has been leveraged by threat…