Author: Cybernoz
CISA’s 11-Month extension ensures continuity of MITRE’s CVE Program Pierluigi Paganini April 16, 2025 MITRE’s U.S.-funded CVE program, a core…
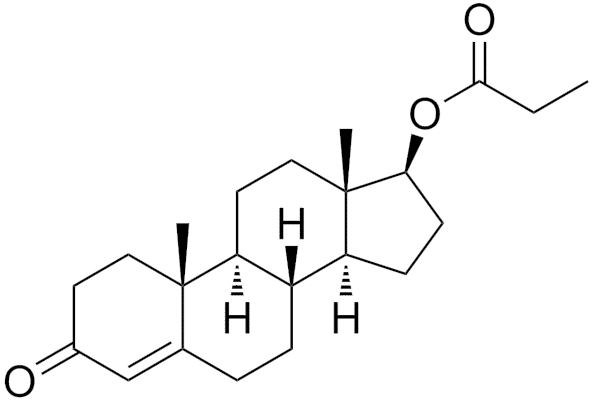
Testosterone does two things to men: 1) it makes them horny, and 2) it makes them more likely to take…
Researchers have uncovered the true identity of servers hosting one of the most notorious ransomware operations active today. The Medusa…
The Cybersecurity and Infrastructure Security Agency (CISA) has extended funding to the MITRE Corporation, ensuring the continued operation of the…
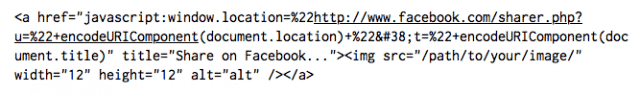
If you’ve messed with getting Facebook buttons on your site you know that there are a couple of ways to…
Google blocked 5.1 billion ads and suspended more than 39.2 million advertiser accounts in 2024, according to its 2024 Ads Safety Report…
Cybercriminals have launched a sophisticated malware campaign leveraging fake PDF-to-DOCX converter websites that mimic the popular legitimate service PDFCandy. The…
The Interlock ransomware intrusion set has escalated its operations across North America and Europe with sophisticated techniques. Not falling under…
I’m thinking about redesigning my theme again and I’m considering a few key design options: single vs. dual sidebars, and,…
Apple released emergency security updates to patch two zero-day vulnerabilities that were used in an “extremely sophisticated attack” against specific…
Cybersecurity experts have identified a sophisticated ransomware threat known as Interlock, which has been quietly expanding its operations since its…
A critical vulnerability in Microsoft Windows, identified as CVE-2025-24054, has been actively exploited in the wild since March 19, 2025,…