Author: Cybernoz
MITRE avoids CVE program shutdown with last-minute contract extension. Questions remain about long-term funding and the future of vulnerability tracking….
Irony is one word that has been getting massacred more and more lately–mostly because it’s become in-fashion to use it…
Two federal lawmakers today introduced a bi-partisan bill that preserves key regulation that facilitates the sharing of cyber-threat data between…
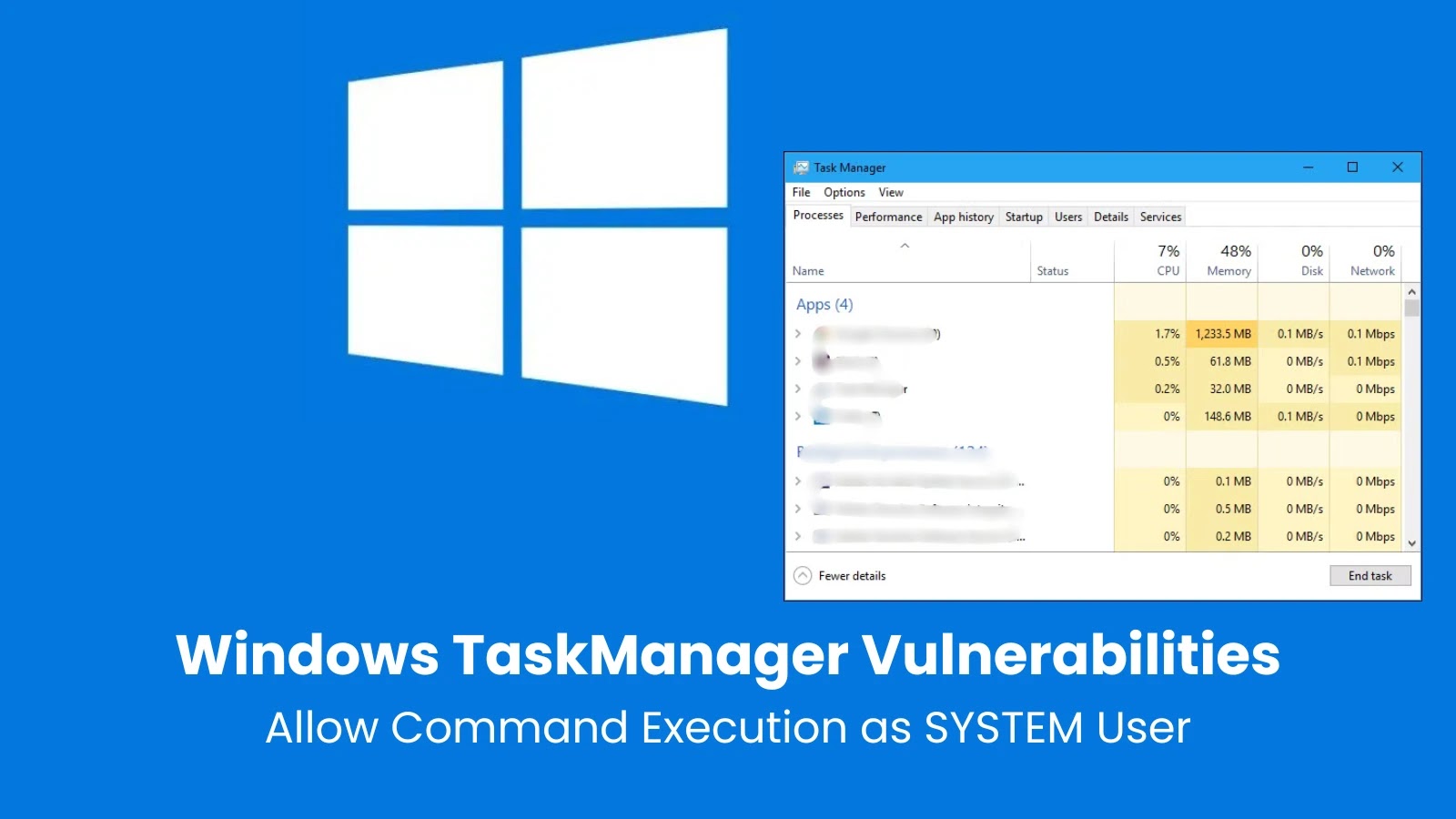
Critical Windows TaskManager involving schtasks.exe binary, which could enable malicious actors to execute commands with SYSTEM-level privileges, bypassing User Account…
CloudSEK’s Security Research team, a sophisticated cyberattack leveraging malicious online PDF converters has been demonstrated to target individuals and organizations…
Over the years, ransomware attacks have become a staple of cybercrime, primarily involving hackers encrypting critical databases and demanding a…
Apr 16, 2025Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have detailed four different vulnerabilities in a core component of the…
All of these bring each other more to mind: here, now, me, us; trend-deviating likely real local events; concrete, context-dependent,…
Attackers have been deploying server-side phishing schemes to compromise employee and member login portals across various enterprises. This strategic shift…
Google, the global search giant and a subsidiary of Alphabet Inc., is rolling out a new security feature dubbed “Auto…
In the wake of the abrupt termination of the Mitre contract to run CVE Programme, a group of vulnerability experts…
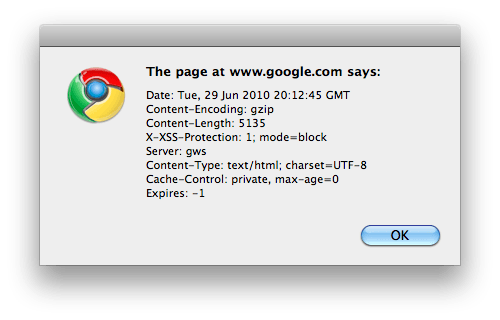
I was looking for a Google Chrome extension that did something like Firefox’s Live HTTP Headers recently and tripped over…