Author: Cybernoz
May 01, 2025Ravie LakshmananVulnerability / VPN Security SonicWall has revealed that two now-patched security flaws impacting its SMA100 Secure Mobile…
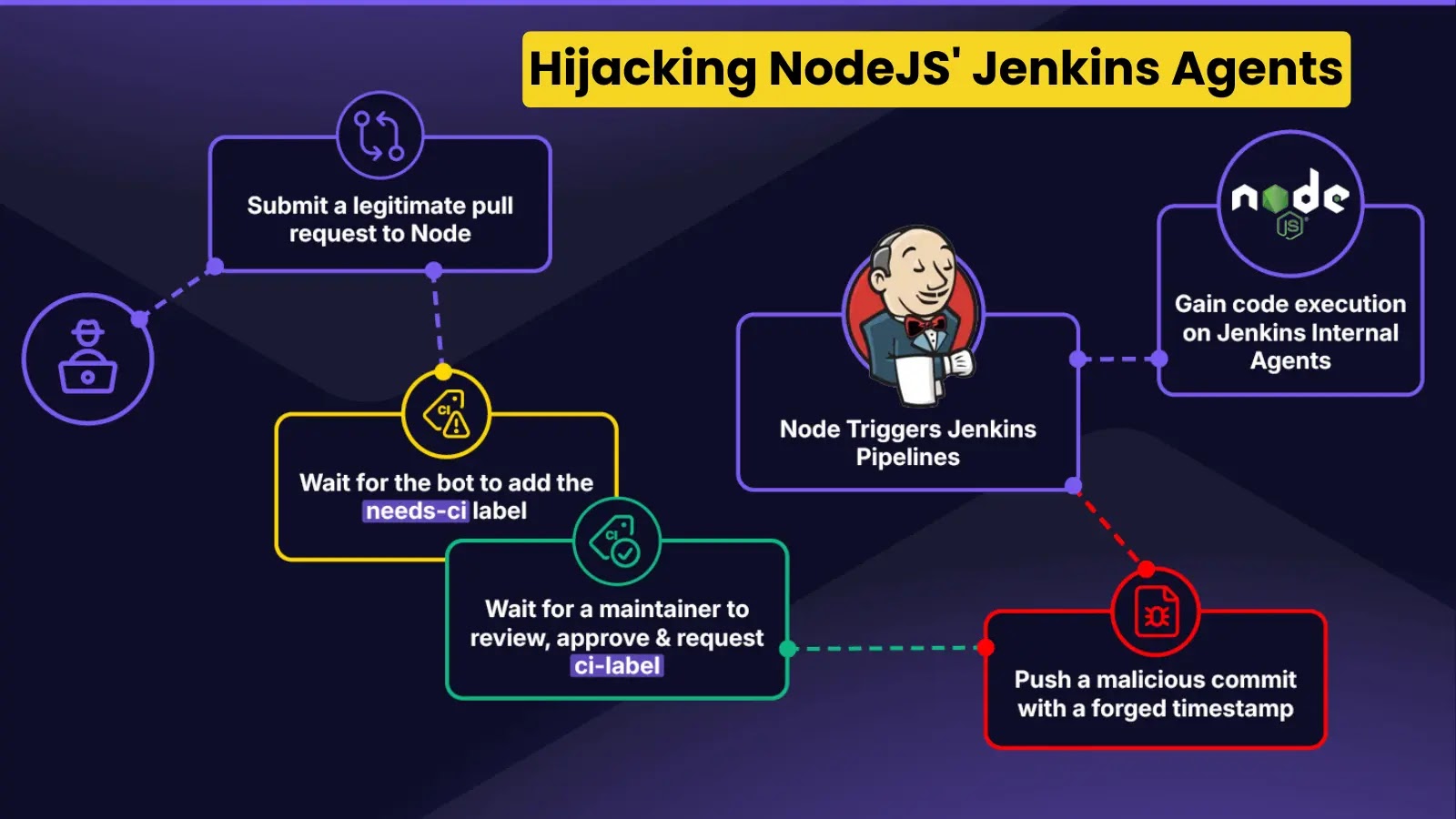
Security researchers recently uncovered a critical vulnerability in Node.js’s continuous integration infrastructure that allowed attackers to execute malicious code on…
Commvault, a global leader in data protection and information management, has confirmed that a sophisticated cyberattack involving a zero-day vulnerability…
One of the most prevalent concerns for security leaders is cost – namely, how they can work within their budget…
In this Help Net Security interview, Steven Furnell, Professor of Cyber Security at the University of Nottingham, illustrates how small…
As we have entered Q2 2025, let’s dive into key improvements and new features introduced on the Intigriti platform in…
A security researcher identified as Remy disclosed a critical vulnerability discovered during a YesWeHack bug bounty engagement. The researcher uncovered…
The Co-Operative Group, commonly known as Co-Op, has issued an official statement confirming that some of its systems were recently…
Machine identities are multiplying fast, and many organizations are struggling to keep up. In this Help Net Security interview, Wendy…
TikTok planned to invest €1 billion (US$1.14 billion) to build its first data centre in Finland as it moved data…
The cybersecurity landscape faces unprecedented challenges as artificial intelligence systems become increasingly weaponized by malicious actors. A groundbreaking report released…
The Tor Project has announced the official release of Tor Browser 14.5.1, introducing a host of security improvements and new…