Author: Cybernoz
A critical 0-day vulnerability has been disclosed in CentreStack, a popular enterprise cloud storage and collaboration platform, which could allow…
Thank you for joining! Access your Pro+ Content below. 15 April 2025 How will Trump’s tariffs hit tech? Share this…
The State of Pentesting Report 2025 pulls back the curtain on how organizations are really doing when it comes to…
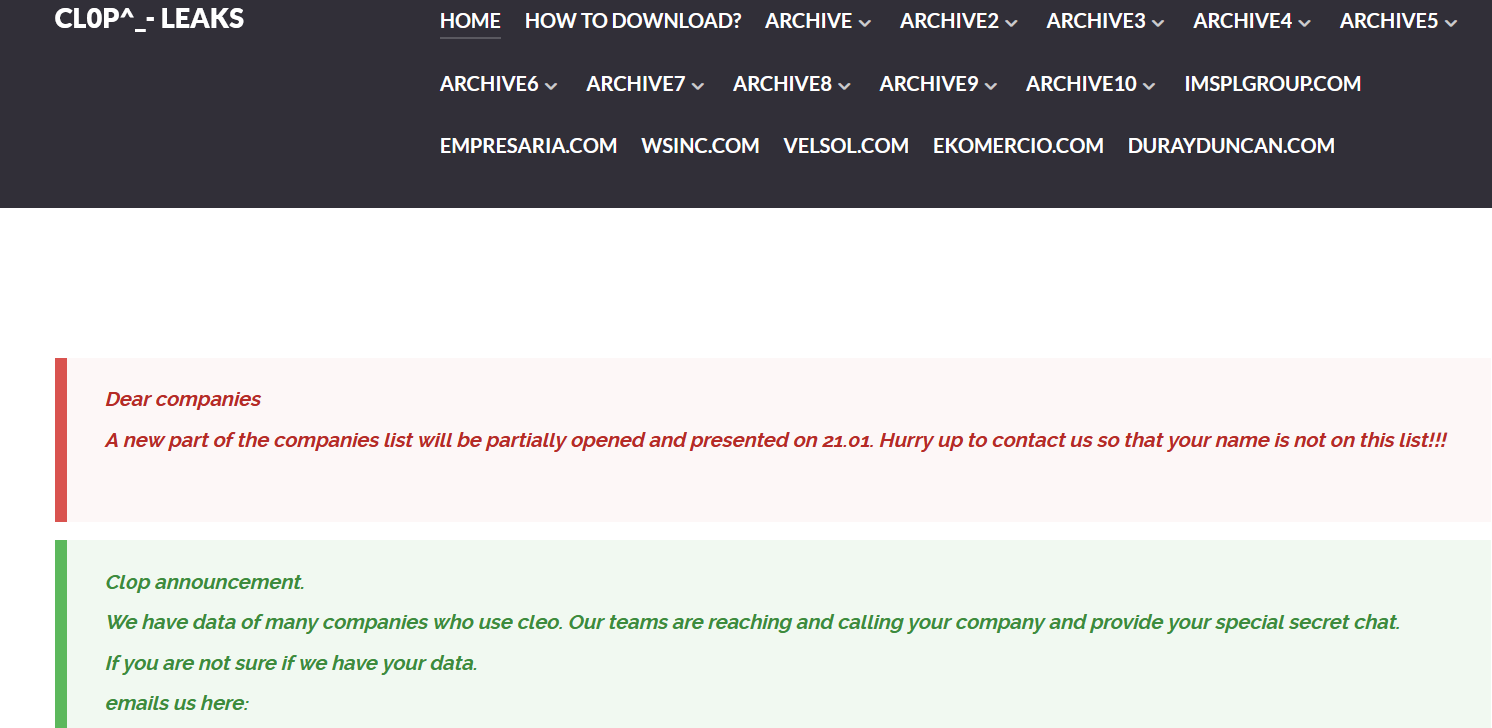
Hertz disclosed a data breach following 2024 Cleo zero-day attack Pierluigi Paganini April 15, 2025 Hertz Corporation disclosed a data…
My friend Richard is very passionate about software patents, and he’s in the process socializing an open letter he recently…
In an era defined by escalating cyber threats and regulatory scrutiny, the role of the Chief Information Security Officer (CISO)…
Over 100,000 WordPress websites have been exposed to a critical security vulnerability, following the public disclosure of a flaw in…
In 2023, the Federal Trade Commission (FTC) released a warning to five of the most popular tax preparation companies, stating…
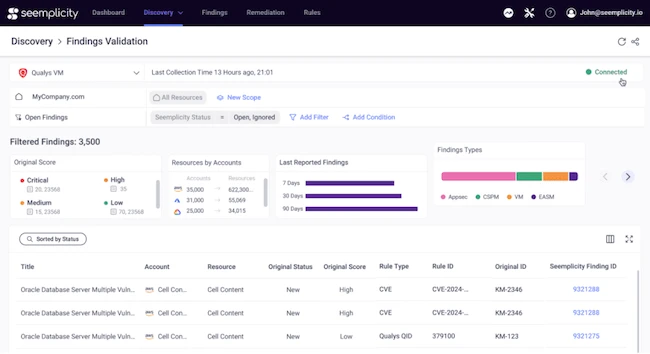
Seemplicity announced a major product release. This latest version of the Seemplicity Platform introduces powerful new AI-driven capabilities designed to…
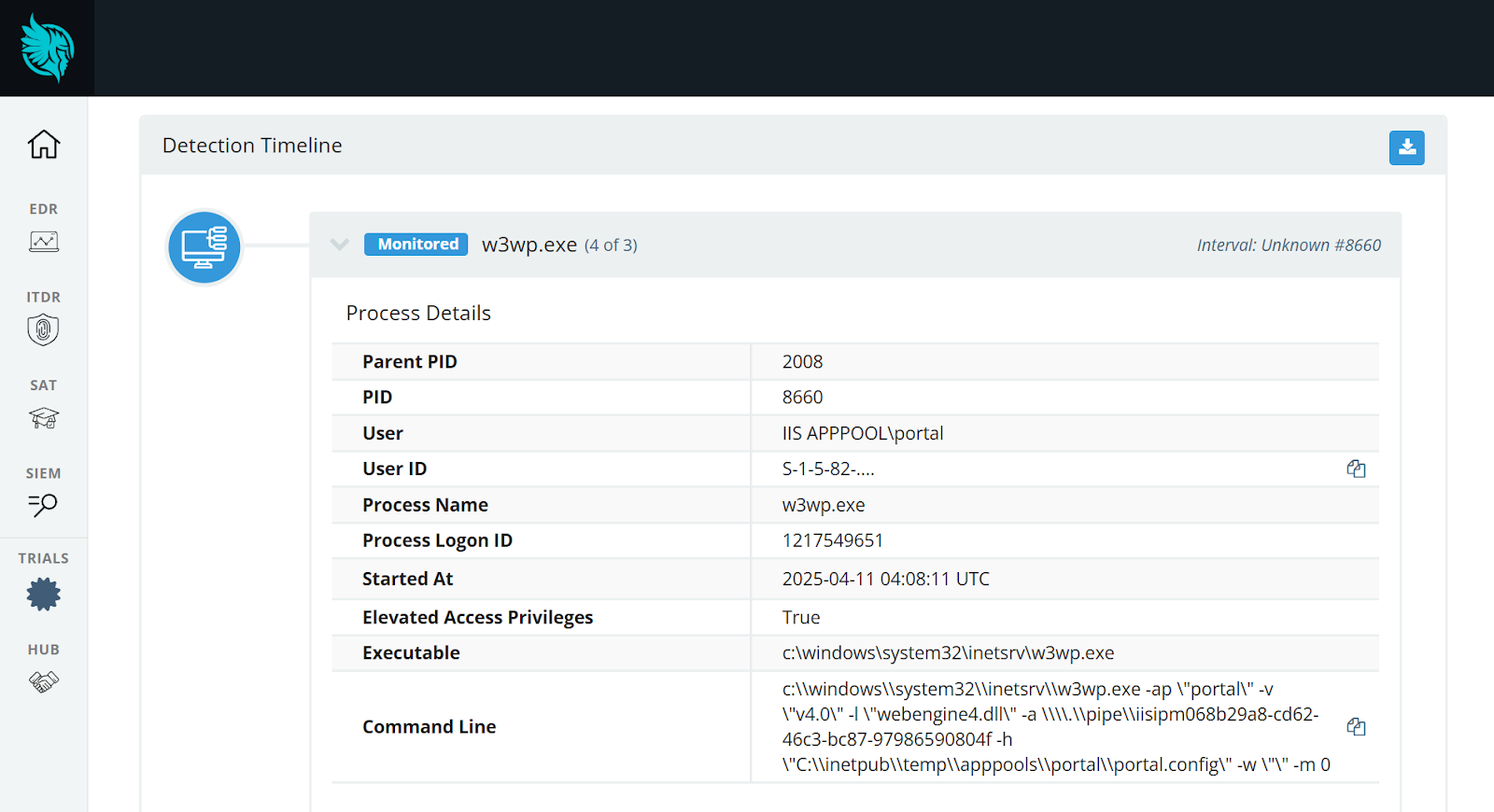
Gladinet flaw CVE-2025-30406 actively exploited in the wild Pierluigi Paganini April 15, 2025 Huntress reports active exploitation of Gladinet CVE-2025-30406…
I find this a highly practical argument, but not an absolute or reality-based one. He’s saying that because humans can…
A new concerning threat has emerged in the cybercriminal ecosystem targeting Apple users. A sophisticated macOS malware-as-a-service offering called “iNARi…