Author: Cybernoz
In 2023, the Federal Trade Commission (FTC) released a warning to five of the most popular tax preparation companies, stating…
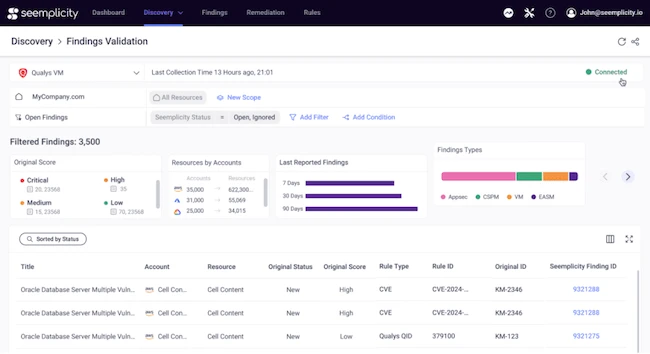
Seemplicity announced a major product release. This latest version of the Seemplicity Platform introduces powerful new AI-driven capabilities designed to…
Gladinet flaw CVE-2025-30406 actively exploited in the wild Pierluigi Paganini April 15, 2025 Huntress reports active exploitation of Gladinet CVE-2025-30406…
I find this a highly practical argument, but not an absolute or reality-based one. He’s saying that because humans can…
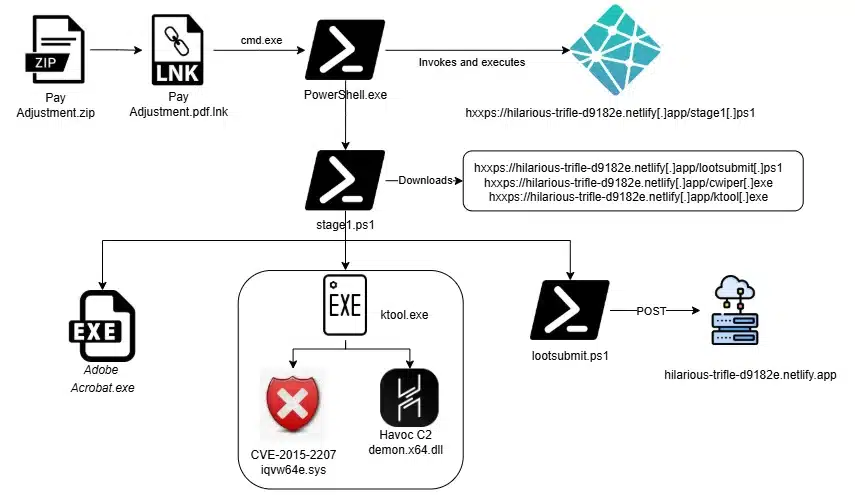
A new concerning threat has emerged in the cybercriminal ecosystem targeting Apple users. A sophisticated macOS malware-as-a-service offering called “iNARi…
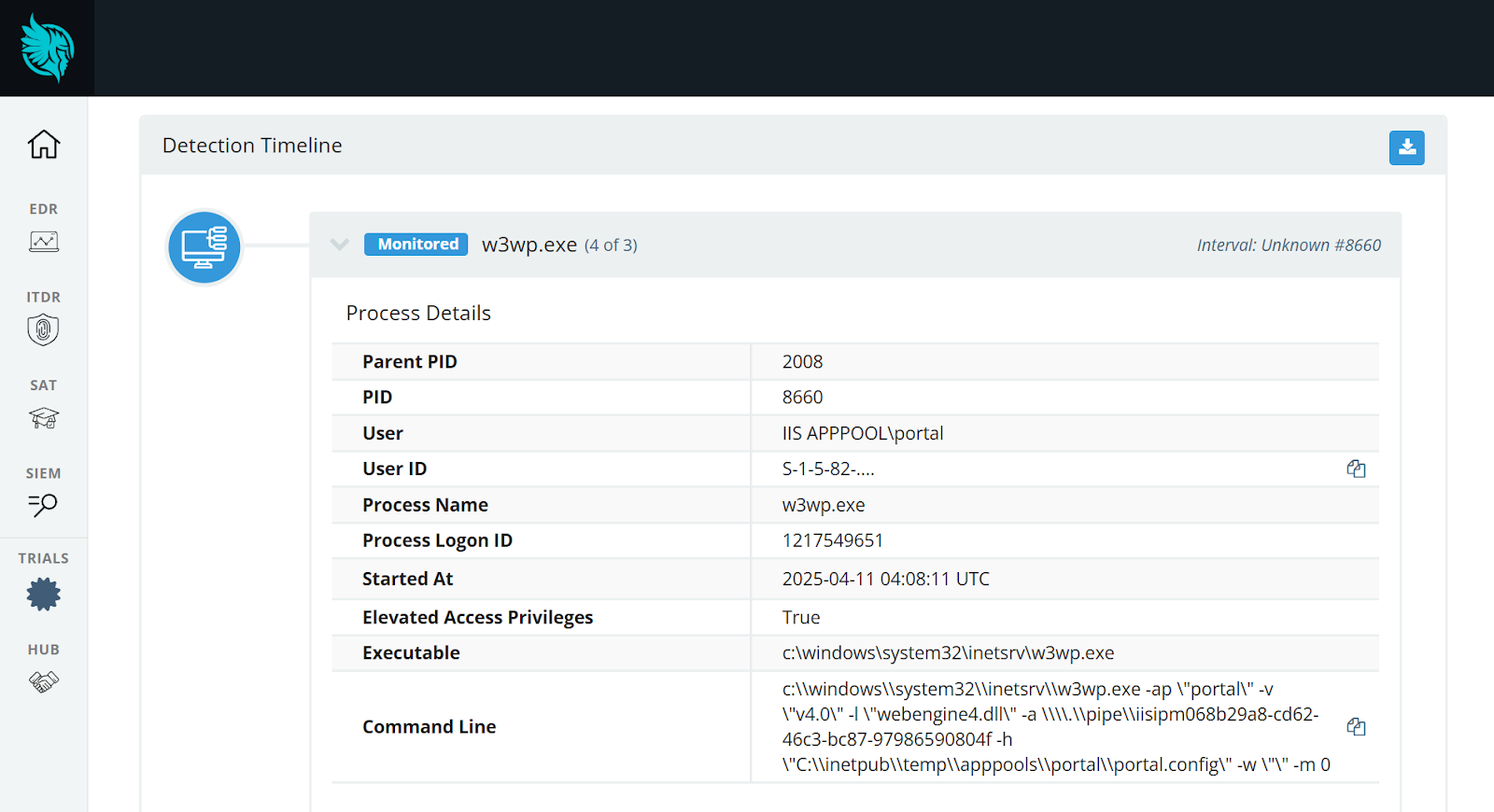
A sophisticated cyberattack campaign has emerged, leveraging Microsoft Teams chats to infiltrate Windows PCs with malware, according to a recent…
Just days after the United States was implicated in launching a series of cyberattacks on the telecom sector under the…
Cyble researchers have uncovered ransomware called DOGE BIG BALLS, a ransomware that not just stands out but also presents its…
So Verizon and Google just announced a strategic partnership. Verizon also stated that they’re embracing openness, which means (among other…
A significant vulnerability in Samsung Galaxy S24 devices that allows network-adjacent attackers to create arbitrary files on affected installations. The…
A newly disclosed vulnerability in Apache Roller, the popular open-source blog server, could allow attackers to bypass critical access controls…
In the wake of a cyberattack, many organizations instinctively believe that shutting down their systems is the quickest and most…