Author: Cybernoz
Apr 15, 2025Ravie LakshmananArtificial Intelligence / Data Privacy Meta has announced that it will begin to train its artificial intelligence…
There are many harsh things about life. The one people grapple with most is death, of course, but I see…
Educational institutions worldwide are facing an unprecedented wave of sophisticated cyber attacks, with the education sector ranked as the third-most…
A security flaw in Samsung’s Quick Share feature for the Galaxy S24 series has been disclosed, enabling attackers to create…
In this Help Net Security interview, Sandy Kronenberg, CEO of Netarx, discusses how cybercriminal groups are adopting corporate structures and…
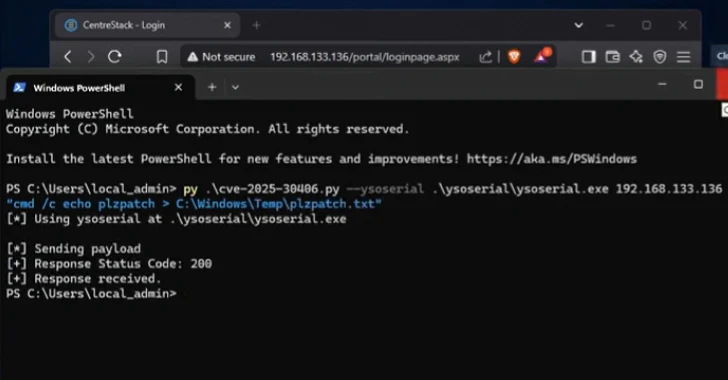
Apr 15, 2025Ravie LakshmananVulnerability / Endpoint Security A recently disclosed security flaw in Gladinet CentreStack also impacts its Triofox remote…
Australian organizations using Fortinet products are being urged to take immediate action following a new advisory highlighting the active exploitation…
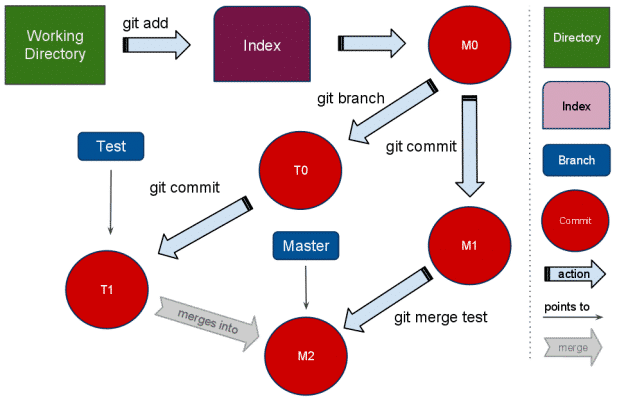
Sometimes when you first install git you realize you added a bunch of crap to your repository, which makes it…
A new sophisticated attack campaign where cybercriminals are exploiting Microsoft Teams to deliver malware and maintain persistent access to corporate…
Across the globe, a new kind of threat is targeting the very institutions dedicated to shaping the future: schools, colleges,…
The Rise of Zero-Click Spyware Recent revelations about a zero-click exploit targeting WhatsApp users underscore the growing threat of sophisticated…
Organizations are fixing less than half of all exploitable vulnerabilities, with just 21% of GenAI app flaws being resolved, according…