Author: Cybernoz
OpenAI has launched its new AI model GPT-4.1, along with smaller versions GPT-4.1 mini and GPT-4.1 nano, touting major improvements…
The majority of conflict within any sufficiently complex debate originates from semantics related to the core terms, e.g. atheist, agnostic,…
Newmont has replaced wi-fi with private 5G to remotely control dozers working in the tailings area of its Cadia gold…
I’m a big fan of nmap‘s –top-ports option, which gives you the ability to leverage Fyodor’s latest Internet research on…
Aussie Broadband is investigating how AI and automation might assist staff with locating information and tapping internal knowledge sources, freeing…
In response to this thread on Reddit: — Free will is a necessary delusion. The big bang happened, and then…
Trend Micro found major flaws in the NVIDIA Container Toolkit and Docker, risking container escapes, DoS attacks and AI infrastructure….
European Facebook users have so far avoided having their public posts used to train parent company Meta’s AI model. That’s…
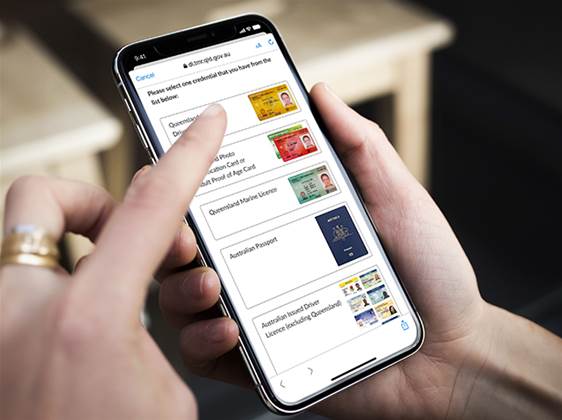
Queensland has officially retired its legacy digital identity system, QGov, after completing the transition to a “modern digital architecture”. The…
What follows is an excellent piece from Reddit on why leaving a religion can be so incredibly difficult. Here is…
American business services giant and government contractor Conduent disclosed today that client data was stolen in a January 2025 cyberattack….
Security and privacy advocates are girding themselves for another uphill battle against Recall, the AI tool rolling out in Windows…