Author: Cybernoz
The Cybercrime Magazine YouTube Channel has reached 1 million subscribers. We are the #1 destination for entertaining and informative videos covering AI and security,…
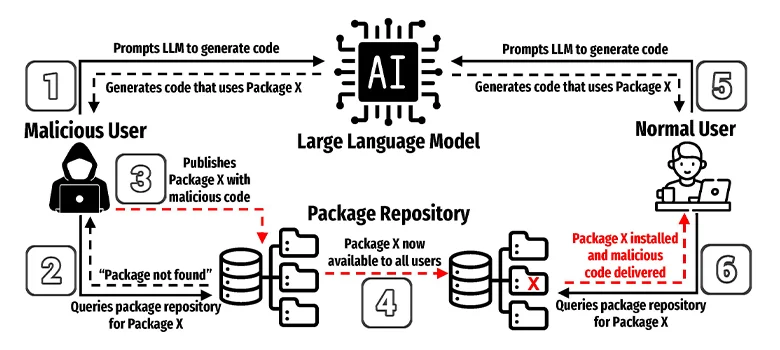
LLMs’ tendency to “hallucinate” code packages that don’t exist could become the basis for a new type of supply chain…
Many of our best people were really bad people. But I read a lot, so I already knew this, and…
According to references on OpenAI’s website, the Microsoft-backed AI startup plans to launch five new models this week, including GPT-4.1,…
Broadcom has officially reintroduced the free version of VMware ESXi with the release of ESXi 8.0 Update 3e (Build 24674464)…
On February 21, the largest crypto heist ever started to unfold. Hackers gained control of a crypto wallet belonging to…
In a concerning report from cybersecurity firm TeamT5, it has been revealed that a Chinese Advanced Persistent Threat (APT) group…
There’s a saying in atheism circles that aims to show Christian hypocrisy related to how they dismiss all the thousands…
Wallarm Research has just released a powerful new Nuclei template targeting a new kind of exposure: the Model Context Protocol…
Major courier firm SF Express has stopped sending text messages to Hong Kong customers with self-pickup parcels and will only…
Microsoft has released out-of-band (OOB) Windows updates to address a known issue affecting local audit logon policies in Active Directory…
Microsoft has warned IT administrators about a critical issue affecting Windows Server 2025 domain controllers. Following a system restart, these…