Author: Cybernoz
Government and telecommunications sectors in Southeast Asia have become the target of a “sophisticated” campaign undertaken by a new advanced…
Attackers chained Craft CMS zero-days attacks in the wild Pierluigi Paganini April 28, 2025 Orange Cyberdefense’s CSIRT reported that threat…
A severe zero-day vulnerability has been uncovered in multiple Viasat satellite modem models, including the RM4100, RM4200, EM4100, RM5110, RM5111,…
A severe vulnerability (CVE-2025-23016) in the FastCGI library-a core component of lightweight web server communication been disclosed, threatening countless embedded…
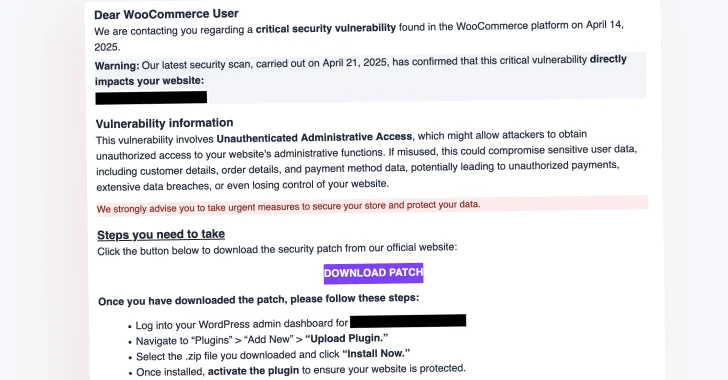
Apr 28, 2025Ravie LakshmananWebsite Security / Malware Cybersecurity researchers are warning about a large-scale phishing campaign targeting WooCommerce users with…
Obfuscation stands as a powerful weapon for attackers seeking to shield their malicious code from defenders. This technique, which deliberately…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
Apr 28, 2025Ravie LakshmananWeb Application Security / Vulnerability Threat actors have been observed exploiting two newly disclosed critical security flaws…
After years of consideration and public comment, the Federal Trade Commission (FTC) has officially updated its Children’s Online Privacy Protection…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Iluka Resources will implement a Honeywell-made distributed control system at its Eneabba rare earths refinery, which is scheduled for commissioning in…
We recently released The Rise of Agentic AI, our API ThreatStats report for Q1 2025, finding that evolving API threats are…