Author: Cybernoz
People struggle with why Twitter is special. It’s special because it counters, better than any other technology, the timeless social…
In an era where cybersecurity teams face overwhelming alert volumes, staff shortages, and ever-evolving threats, Radiant Security has introduced a…
One of the most common arguments from the religious is that without God there would be no morality. Non-believers reject…
There are three fundamental ways of learning about the world, and they map well to concepts we’re all familiar with:…
China admitted its role in Volt Typhoon cyberattacks on U.S. infrastructure Pierluigi Paganini April 13, 2025 China admitted in a…
It’s getting exciting in the world of cross-network authentication. Let’s review. I can now: We’re quickly approaching the point where…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft fixes actively exploited Windows…
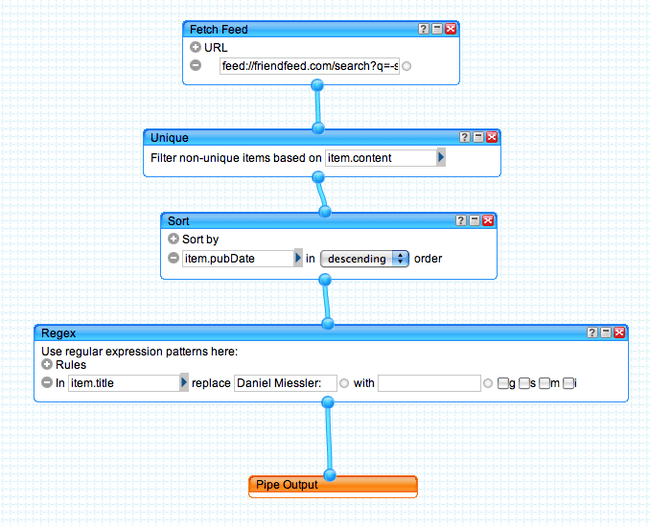
May 4, 2009 One of the things I’ve always found lacking with the various types of RSS feeds available from…
In today’s digital world, passwords alone are not enough to keep our online accounts safe. Cybercriminals are constantly finding ways…
In the spirit of improving my debating skills (both written and oral) I’m setting out on a short project to…
In a troubling development for enterprise cloud users, federal authorities are investigating a major data breach involving Oracle—one of the…
Image from the Star Tribune This boy will likely die soon as a direct result of a false belief. His…