Author: Cybernoz
In a troubling development for enterprise cloud users, federal authorities are investigating a major data breach involving Oracle—one of the…
Image from the Star Tribune This boy will likely die soon as a direct result of a false belief. His…
Here’s an interesting question: what is your standard for deciding when to add a given person to these various services?…
I’ve been using Verisign VIP for a while now with a hard token like the one seen below. It allows…
For Facebook to be as big as it is, it seems like it’d be easier to answer the question that…
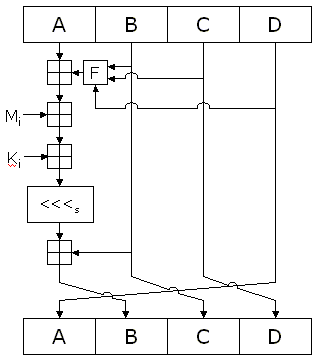
There’s an issue with md5sum where it returns unexpected results due to the fact that appends a carriage return to…
So my buddy Steve brought me a small sample of Jamaican Blue Mountain coffee today. Evidently a co-worker was brewing…
This is one of my favorite programs that NPR does, and if you haven’t partaken of it I highly suggest…
The Trump administration has sought to revoke the parole of some 532,000 Cubans, Haitians, Nicaraguans, and Venezuelans who entered the…
I think the worst part of facing the unexpected death of a loved one is the silence of the dead…
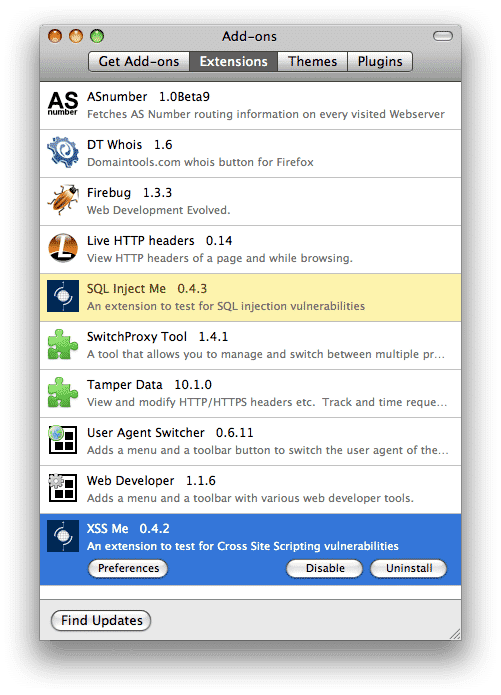
I’ve moved to Chrome and Safari as my primary browsers, but nothing compares to Firefox when it comes to functionality…
One of the things that irks me is really smart people who still deny that the concept of IQ, the…