Author: Cybernoz
I think the worst part of facing the unexpected death of a loved one is the silence of the dead…
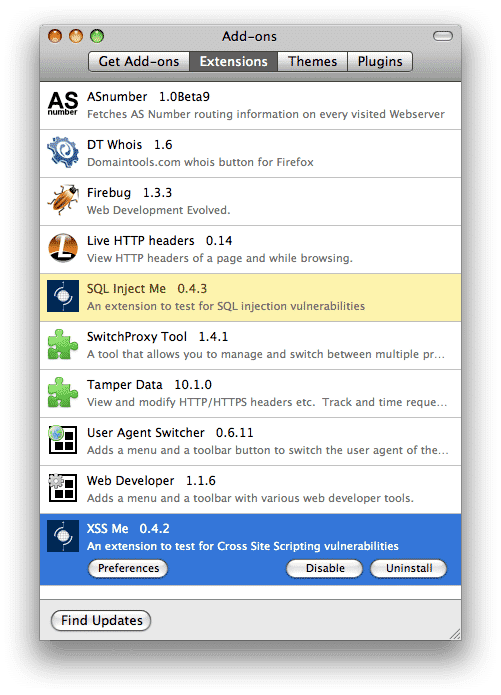
I’ve moved to Chrome and Safari as my primary browsers, but nothing compares to Firefox when it comes to functionality…
One of the things that irks me is really smart people who still deny that the concept of IQ, the…
Few Christians have ever heard in church, or read themselves, the story of the Cannanite woman with a sick daughter….
At this point, FriendFeed’s real purpose is to give users a glimpse of what’s to come for social networking in…
I’m often asked by my smart friends: The answer is simple: religion’s business is to get into my business. When…
Ok, just a few random thoughts; I’ll do a real post later on this once things are fleshed out more….
September 4, 2009 — After much spirited debate I have come to the conclusion that the argument presented below is…
[ 2009-04-12 : I’ve decided to back off this specific argument of “atheist” applying to those that lack belief. The…
I observe three basic types of people working in the IT field: kings, sages, and cogs. The King The king…
It is considered good social networking etiquette–especially on Twitter–to warn your followers that you are posting a link to content…
A new class of supply chain attacks named ‘slopsquatting’ has emerged from the increased use of generative AI tools for…