Author: Cybernoz
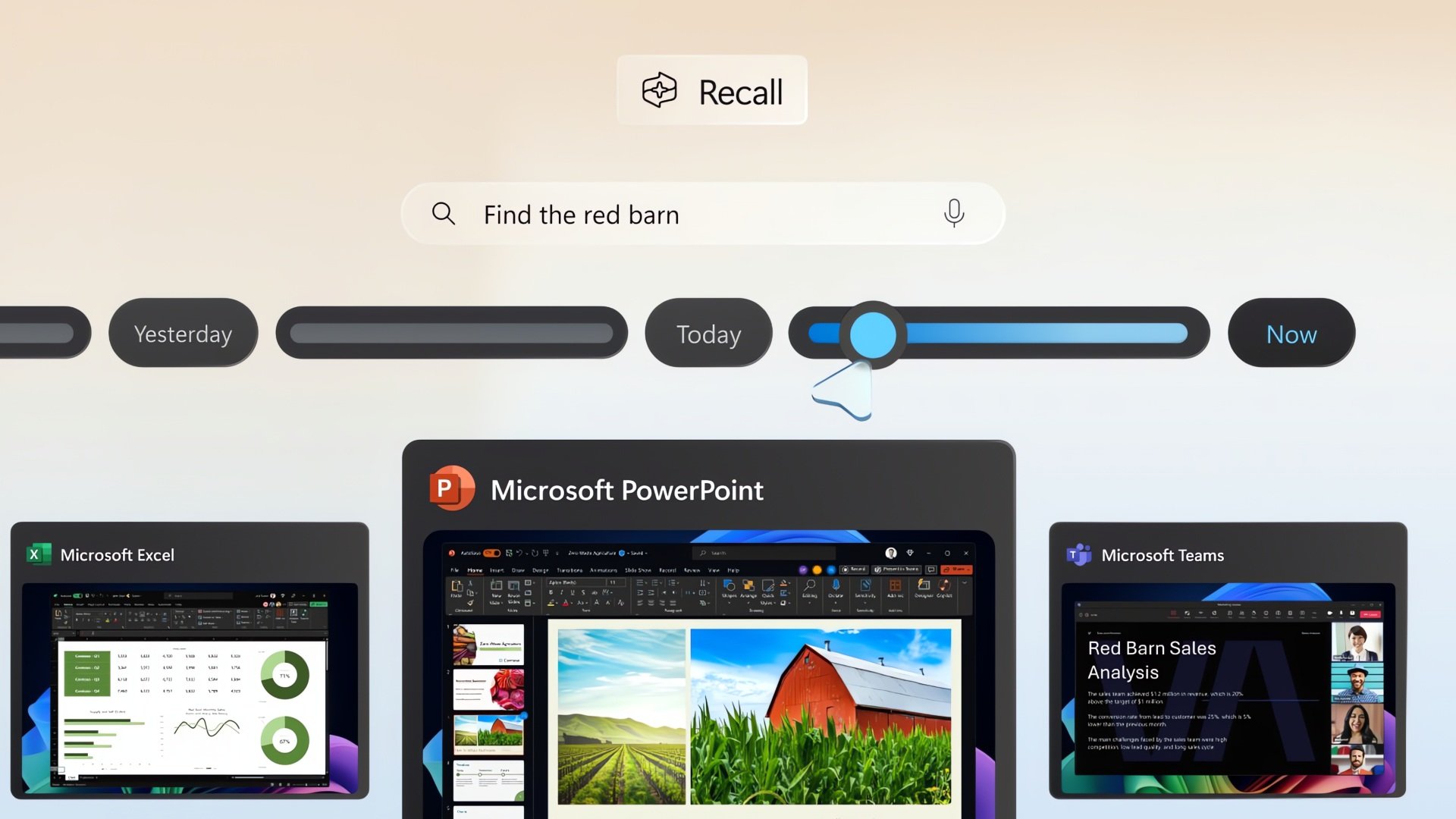
Microsoft is gradually rolling out the AI-powered Windows Recall feature to Insiders in the Release Preview channel before making it…
Smart meters are essential to smart grids, empowering utilities and smart grid managers to provide consumers and energy providers with…
TL;DR: A critical deserialization vulnerability (CVSS 9.8 – CVE-2025-27520) in BentoML (v1.3.8–1.4.2) lets attackers execute remote code without authentication. Discovered…
We all have a problem keeping up with friends and family that have moved away. The problem is simple: we,…
Dive Brief: Fortinet detailed new exploitation activity against known critical vulnerabilities in FortiGate devices, including CVE-2022-42475, CVE-2023-27997 and CVE-2024-21762, in a Thursday…
Western Sydney University (WSU) announced two security incidents that exposed personal information belonging to members of its community. WSU is…
Table Tennis is my sport. It has been since the late 90’s. I’ll not go into my many reasons for…
Dive Brief: Cybersecurity threats emerged as tech executives’ top challenge and area for investment, according to a report published Tuesday…
Fortinet warns that threat actors use a post-exploitation technique that helps them maintain read-only access to previously compromised FortiGate VPN…
In recent years, we’ve become familiar with ransomware attacks, where hackers infiltrate computer networks, encrypt files, and demand payment in…
The US State Department reportedly plans to sign an international agreement designed to govern the use of commercial spyware known…
So I now have fully functioning VOIP at the house using Asterisk, but I currently only have a soft phone,…