Author: Cybernoz
Google’s AI video generator tool Veo 2, which is the company’s take on OpenAI’s Sora, is now rolling out to…
Maintaining work-life balance has been the biggest challenge many women in the technology industry have come up against, according to…
I’ve changed the color and increased the font size on my Twitter posts on the right. I’ve done this for…
Hello Hackers Spring is in the air, and so is the sweet scent of freshly reported bugs. Intigriti’s blooming too—each…
Microsoft has now confirmed that an April 2025 Windows security update is creating a new empty “inetpub” folder and warned…
INE Security Highlights How Practical, immersive training environments help defense contractors meet DoD cybersecurity requirements Defense contractors are facing increased…
The Home Office is operating at least eight artificial intelligence (AI)-powered surveillance towers along the South-East coast of England, which…
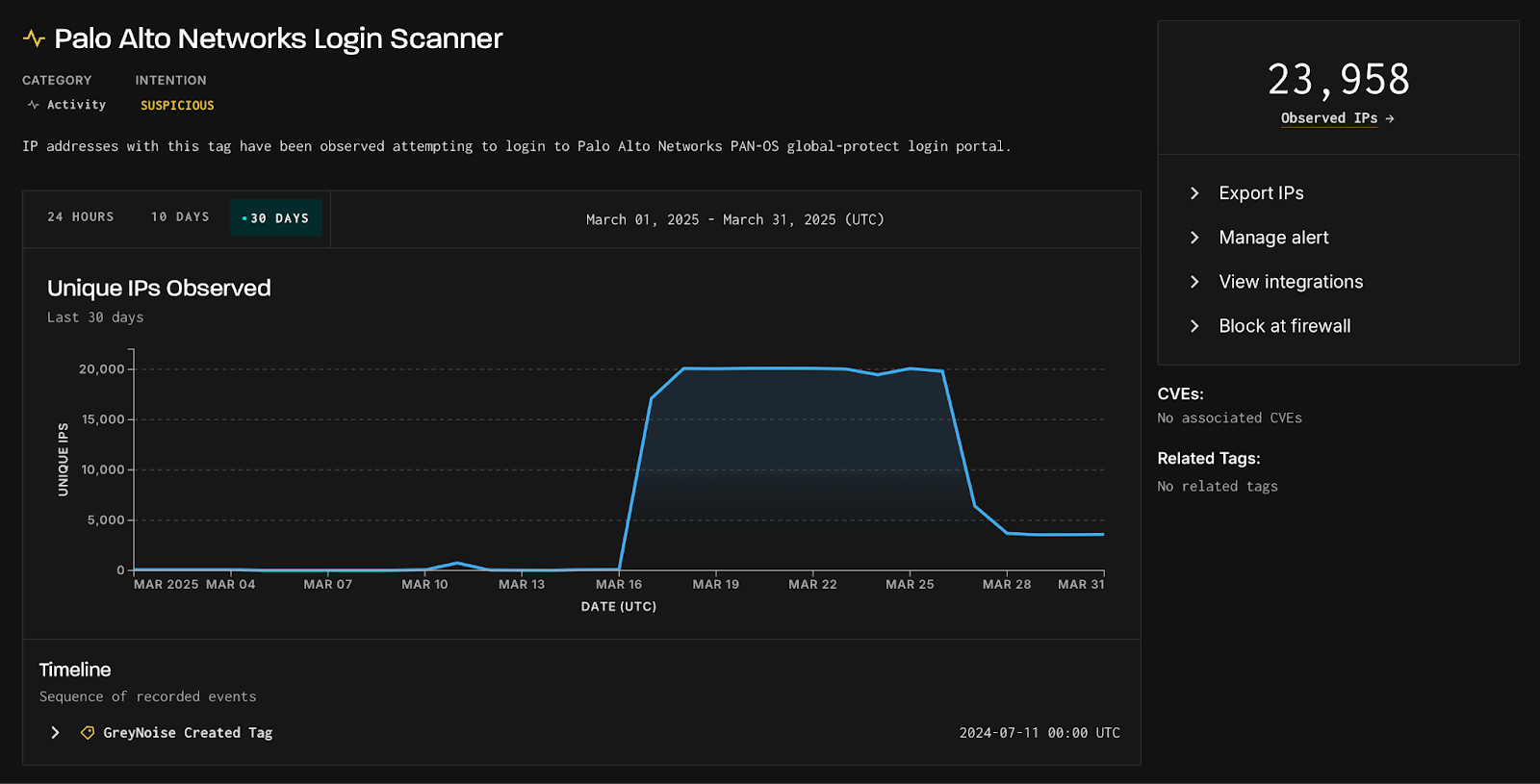
Palo Alto warns of brute-force login attempts on PAN-OS GlobalProtect gateways indicating possible upcoming attacks Pierluigi Paganini April 11, 2025…
I’ve been thinking a lot about life lately–specifically about what, if anything, gives it meaning. I’ve been enumerating the things…
The Chromium-based Microsoft Edge has seen up to 9% performance improvements following the release of version 134. In a blog…
The threat actor known as Paper Werewolf has been observed exclusively targeting Russian entities with a new implant called PowerModul….
[ Published: Jan 4, 2009 ] I’m trying to come up with a simple decision tree, or flowchart, for when…