Author: Cybernoz
Today, in the age of quantum threats, AI and sophisticated digital manipulations, the question is: where does the human factor…
What are IABs? Initial Access Brokers (IABs) specialize in gaining unauthorized entry into computer systems and networks, then selling that…
A report in the Financial Times that European Union (EU) president Ursula von der Leyen could impose tariffs on US…
One of the reasons people don’t want to leave Firefox for Google’s new Chrome Browser is Firefox’s Quicksearch feature, which…
All of the 400 exposed AI systems found by UpGuard have one thing in common: They use the open source…
Microsoft has fortified its Exchange Server and SharePoint Server security by integrating advanced Antimalware Scan Interface (AMSI) capabilities. This measure,…
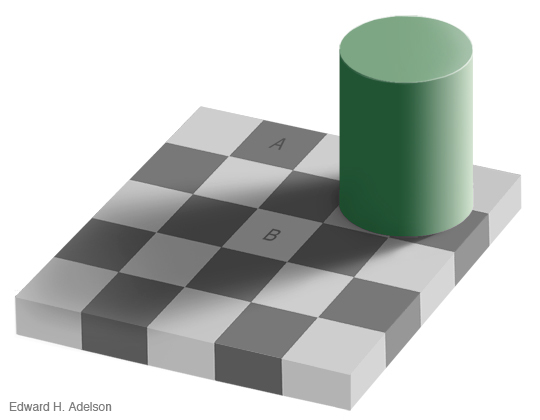
[ Published: Dec 26, 2008 ] A and B are exactly the same shade of gray. This essay is about…
Smishing Triad, a Chinese eCrime group, has launched an extensive operation targeting users across more than 121 countries. This campaign,…
Cybersecurity researchers have found that threat actors are setting up deceptive websites hosted on newly registered domains to deliver a…
I think if I were to have to guess, I would say that the reason we exist–or, to be more…
Cybersecurity experts at Sublime have uncovered a complex malware campaign revolving around TROX Stealer, an information stealer that employs urgency…
Apr 11, 2025Ravie LakshmananVulnerability / Network Security Palo Alto Networks has revealed that it’s observing brute-force login attempts against PAN-OS…