Author: Cybernoz
The pioneering multi-media artist reveals the creative process behind her stage show called ARK, which challenges audiences to reflect on…
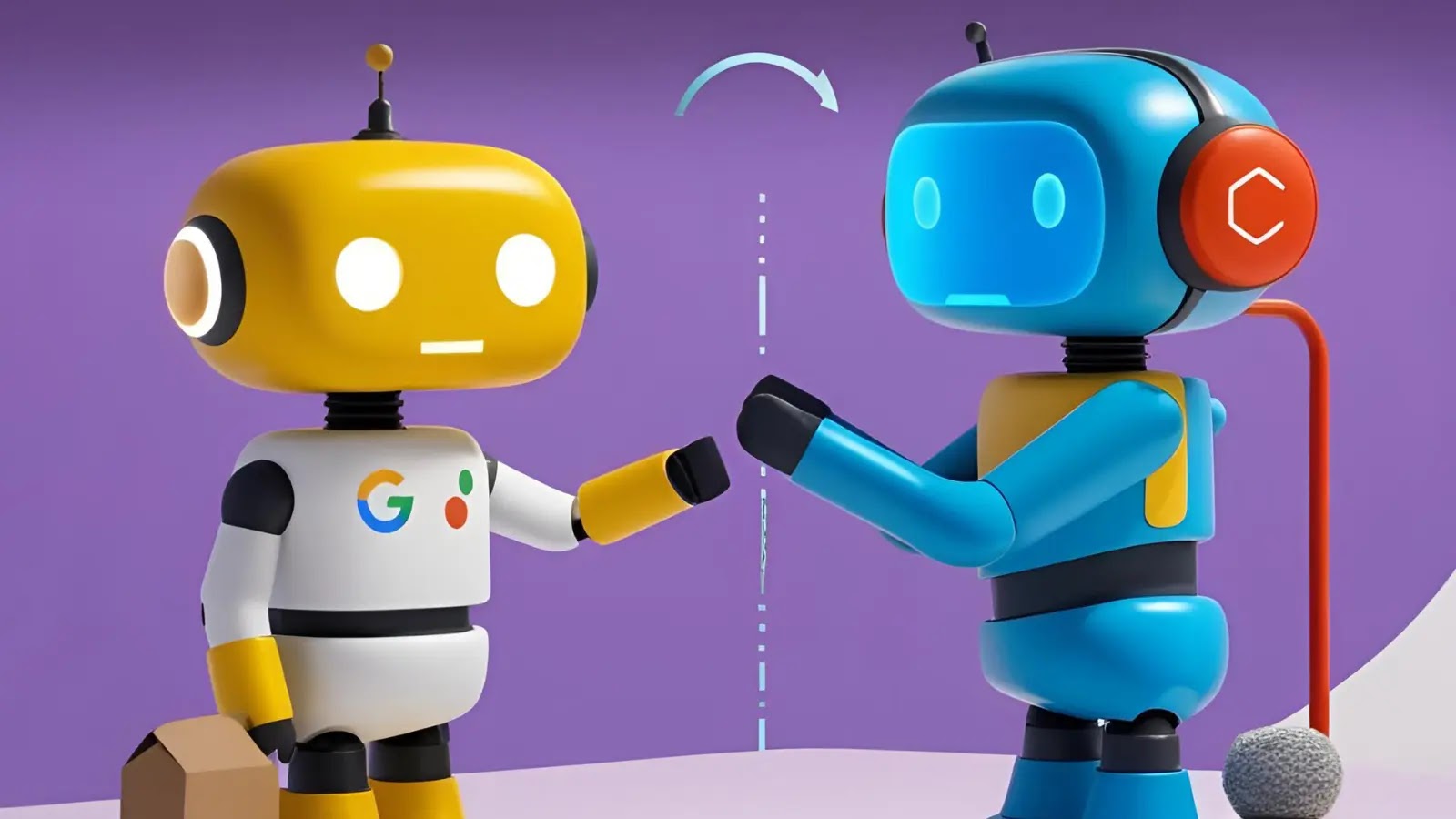
Google Cloud announced the launch of a pioneering open protocol named Agent2Agent (A2A), aiming to revolutionize how AI agents interact…
TL;DR – ReversingLabs has identified a malicious npm package, “pdf-to-office,” that targets Atomic and Exodus crypto wallet users by silently…
Western Sydney University has experienced its fourth cyber incident in two years, this time affecting the data of 10,000 current…
I like the way Whole Foods makes me feel, but I don’t like the fact that it makes me feel…
Ransomware payments trending down, the cyber-resilience gap facing SMBs, and APT groups embracing generative AI – it’s a wrap on…
RansomHub, a leading Ransomware-as-a-Service (RaaS) group that emerged in early 2024, has found itself grappling with internal turmoil. The instability…
U.S. CISA adds Linux Kernel flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini April 10, 2025 U.S. Cybersecurity and Infrastructure…
I have a wicked crazy idea. What if we in the information security community were to organize a campaign to…
A panel of U.S. judges considering an appeal of a ruling that went against El Salvadoran journalists suing NSO Group…
With AI’s pattern recognition capabilities well-established, Mr. Schölkopf’s talk shifts the focus to a pressing question: what will be the…
Hackers started exploiting a high-severity flaw that allows bypassing authentication in the OttoKit (formerly SureTriggers) plugin for WordPress just hours after…