Author: Cybernoz
For anyone interested in Information Security certifications, the GIAC GSE one to keep on your mental radar. It’s a SANS…
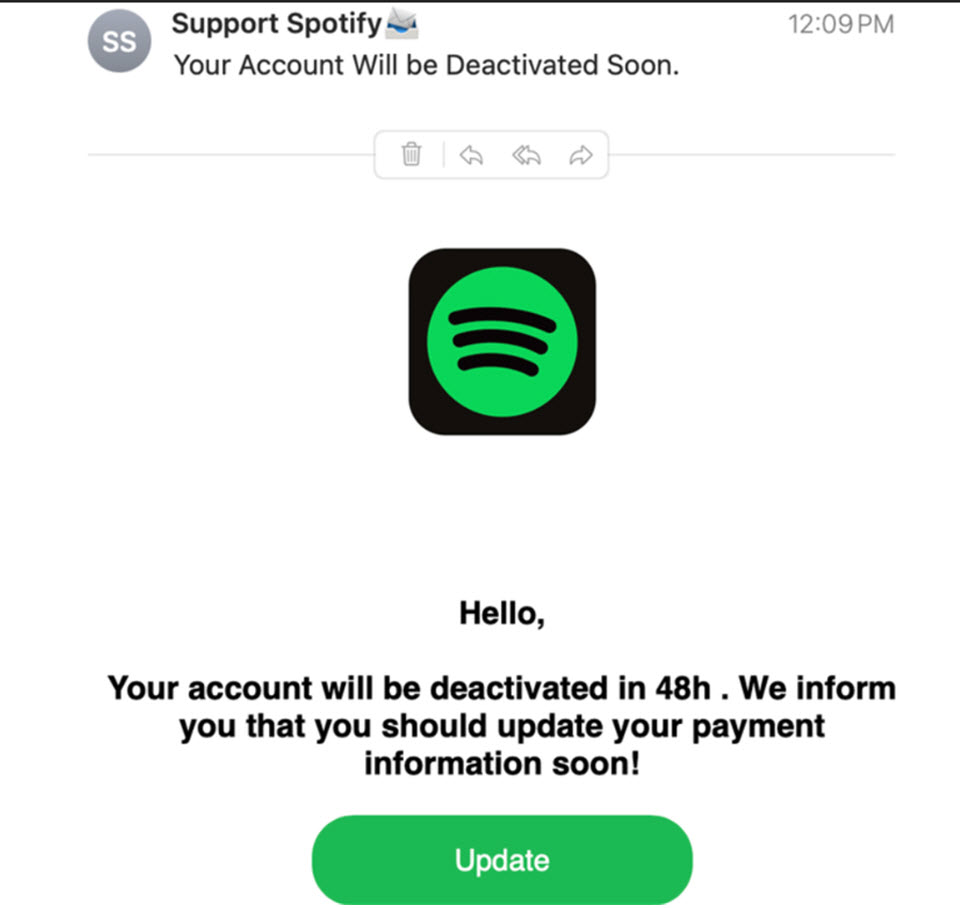
Spotify boasts almost 700 million active users, including 265 million premium subscribers. As the world’s leading music streaming service, it’s…
Claude has a new subscription tier called “MAX,” but it costs a whopping $200 per month, and users aren’t happy…
China-based purveyors of SMS phishing kits are enjoying remarkable success converting phished payment card data into mobile wallets from Apple…
AhnLab Security Intelligence Center (ASEC) has unearthed a complex cyber campaign in which attackers, suspected to be Arabic speakers, have…
TL;DR: The hammer’s coming down not just on malware creators but the users funding them. If you paid to compromise…
Ransomware attacks are known to frequently occur over weekends, and Sensata Technologies, a prominent manufacturer of sensors and electrical components…
The greatest achievement is selflessness. The greatest worth is self-mastery. The greatest quality is seeking to serve others. The greatest…
On March 25, 2025, NIST released the initial public draft of NIST SP 800-228, “Guidelines for API Protection for Cloud-Native…
While relatively rare, real-world incidents impacting operational technology highlight that organizations in critical infrastructure can’t afford to dismiss the OT…
Microsoft is investigating a potential licensing issue blocking access to Microsoft 365 services for some customers with Family subscriptions. After…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…