Author: Cybernoz
TL;DR: The hammer’s coming down not just on malware creators but the users funding them. If you paid to compromise…
Ransomware attacks are known to frequently occur over weekends, and Sensata Technologies, a prominent manufacturer of sensors and electrical components…
The greatest achievement is selflessness. The greatest worth is self-mastery. The greatest quality is seeking to serve others. The greatest…
On March 25, 2025, NIST released the initial public draft of NIST SP 800-228, “Guidelines for API Protection for Cloud-Native…
While relatively rare, real-world incidents impacting operational technology highlight that organizations in critical infrastructure can’t afford to dismiss the OT…
Microsoft is investigating a potential licensing issue blocking access to Microsoft 365 services for some customers with Family subscriptions. After…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Apr 10, 2025Ravie LakshmananContainer Security / Vulnerability Cybersecurity researchers have detailed a case of an incomplete patch for a previously…
With support from technology partners, Google has introduced an open agent-to-agent protocol to enable artificial intelligence (AI) agents to communicate securely…
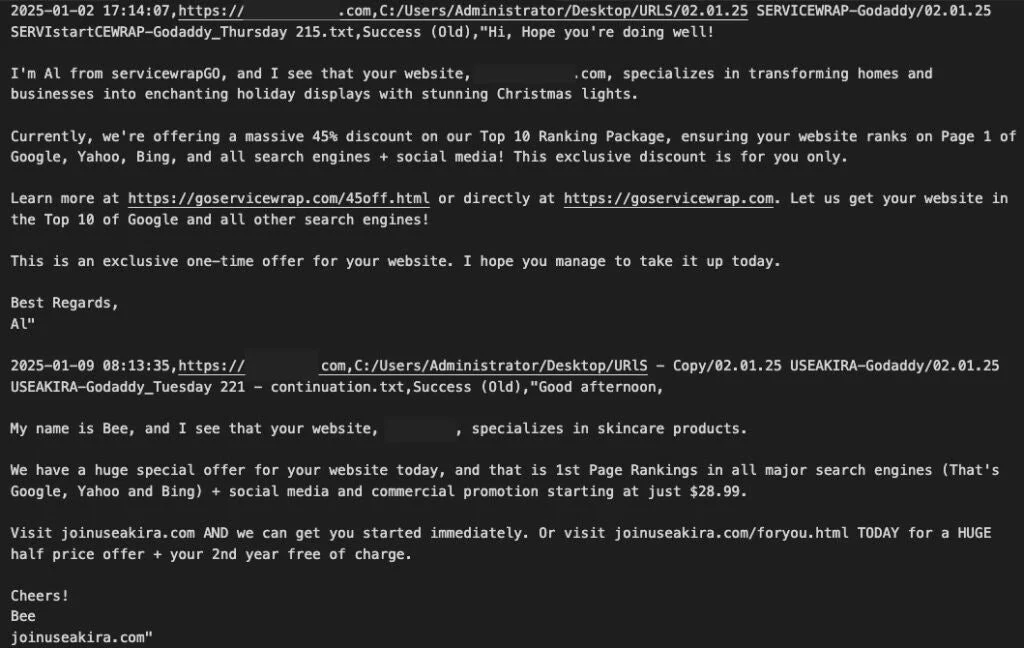
AkiraBot: AI-Powered spam bot evades CAPTCHA to target 80,000+ websites Pierluigi Paganini April 10, 2025 AkiraBot, a CAPTCHA-evading Python framework,…
Image from weber.edu As I sit here at my allergist waiting on the all-clear after my shots, I’m thinking about…
Tom Ryder | 10 April 2025 at 14:33 UTC When we wrapped up our biggest-ever webinar, The Future of AppSec:…