Author: Cybernoz
A critical security vulnerability has been discovered in the Langflow AI Builder, a popular tool for creating agentic AI workflows….
US President Donald Trump has signed an Executive Order on Wednesday to revoke security clearance held by Chris Krebs, the…
Senator Cassidy, the chair of the US Senate Health, Education, Labor, and Pensions Committee has expressed concerns about foreign adversaries,…
Apr 10, 2025The Hacker NewsAI Security / Enterprise Security AI agents have rapidly evolved from experimental technology to essential business…
It’s not that their logical arguments are slightly more emotional than democratic logical arguments; they’re actually purposely avoiding logic altogether….
ESET researchers also examine the growing threat posed by tools that ransomware affiliates deploy in an attempt to disrupt EDR…
Microsoft 365 Family subscribers are currently facing disruptions in accessing their services due to a potential licensing issue, as confirmed…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Overview of the PlayPraetor Masquerading Party Variants CTM360 has now identified a much larger extent of the ongoing Play Praetor…
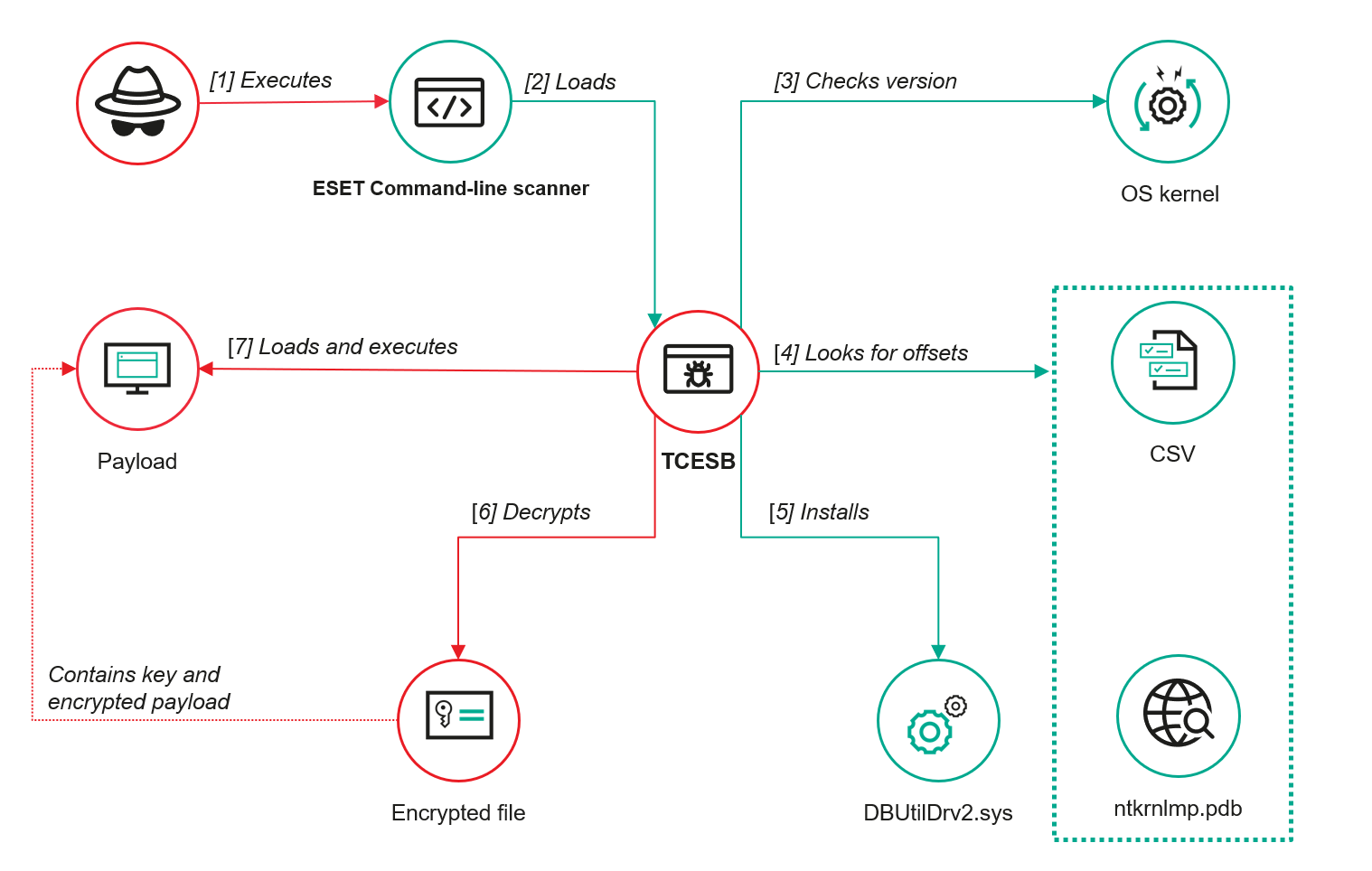
An APT group exploited ESET flaw to execute malware Pierluigi Paganini April 10, 2025 At least one APT group has…
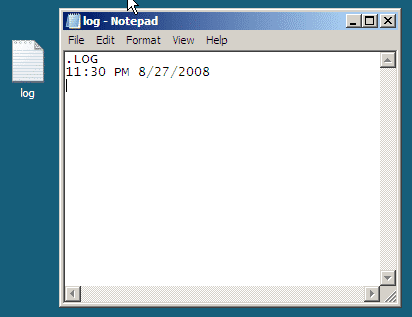
Yeah, that Notepad. It has a feature that few know about, and I’m not talking about word wrap. You can…
Security awareness training doesn’t have to be a snoozefest – games and stories can help instill ‘sticky’ habits that will…