Author: Cybernoz
US cities are warning of an ongoing mobile phishing campaign pretending to be texts from the city’s parking violation departments about…
Undocumented hidden feature found in Espressif ESP32 microchip Pierluigi Paganini March 09, 2025 Experts discovered an undocumented hidden feature in…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: How QR code attacks work…
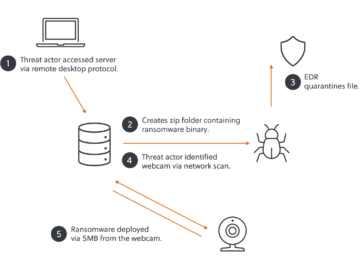
Akira ransomware gang used an unsecured webcam to bypass EDR Pierluigi Paganini March 08, 2025 The Akira ransomware gang exploited…
Japanese telecom giant NTT suffered a data breach that impacted 18,000 companies Pierluigi Paganini March 08, 2025 A data breach…
A software developer has been found guilty of sabotaging his ex-employer’s systems by running custom malware and installing a “kill switch”…
The ubiquitous ESP32 microchip made by Chinese manufacturer Espressif and used by over 1 billion units as of 2023 contains…
Cybercriminals are sending bogus copyright claims to YouTubers to coerce them into promoting malware and cryptocurrency miners on their videos….
Push notifications are a common feature that many websites use to keep users engaged. However, what happens when these notifications…
Business executives never think they’ll be victims of a cyberattack until it happens to them—and by that point, it’s already…
As Donald Trump’s administration continues its relentless reorganization of the United States federal government, documents obtained by WIRED showed this…
AI applications are embedded in our phones and becoming a vital part of life. To accelerate mainstream adoption, technology companies…