Author: Cybernoz
I’ve been having a long-running debate with two other hardcore gamer friends of mine about a comment that was made…
In the ever-evolving world of cybersecurity, the ability to detect threats quickly and accurately is crucial for defending modern digital…
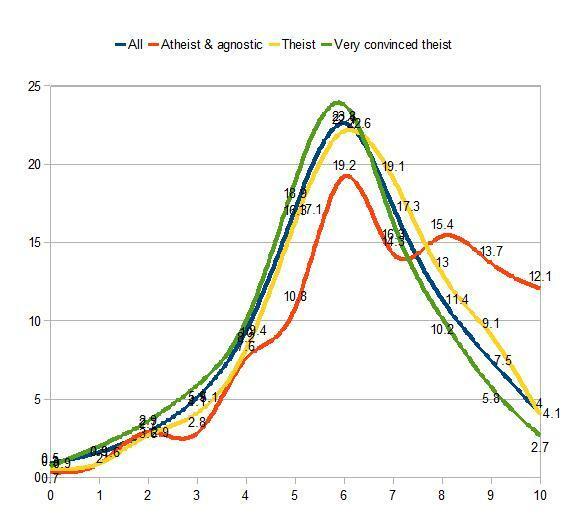
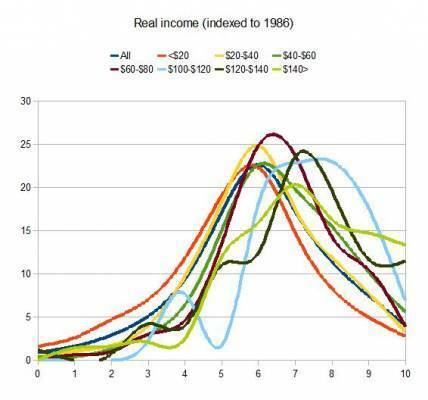
Gene Expression recently put up a brilliant post showing data on the GSS‘s WORDSUM scores correlated to various demographic data…
The discovery of a compromised endpoint in an organization’s network marks the beginning of what can be a complex forensic…
I had an idea the other day about life achievement: if you currently have no plans to be worthy of…
Gamification is a trend in technology right now where people are given micro rewards for accomplishing discrete tasks, such as…
SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 42 Pierluigi Paganini April 20, 2025 Security Affairs Malware newsletter includes a collection of the…
People tend to love Starbucks despite their coffee tasting like it was brewed for three weeks in the center of…
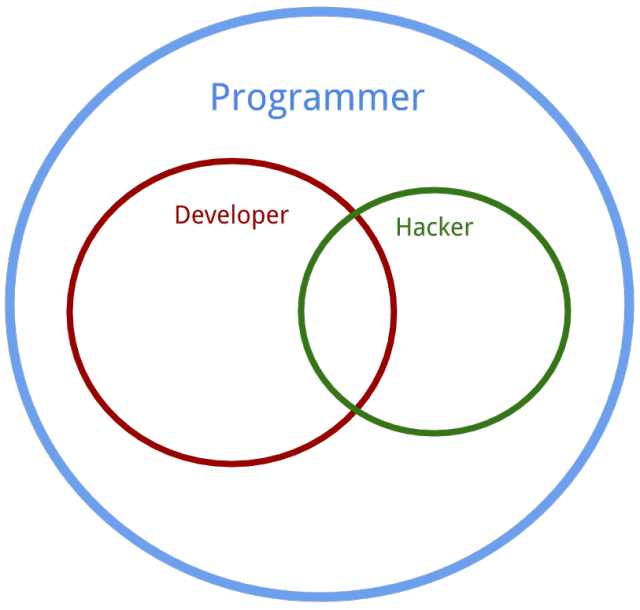
There is often spirited discussion and debate about the differences between Programmers, Hackers, and Developers. Most descriptions I’ve seen are…
In everyday life, AI integration rapidly changes traditional consumers’ shopping experiences, changes work scenarios at work spots, and health provision….
[ The graph’s x-axis shows the GSS WORDSUM score, which is a vocabulary-based intelligence proxy (correlated at .71). The y-axis…
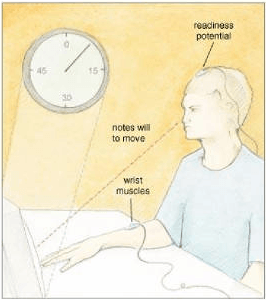
Image from skeptically.org In my ongoing efforts to convince others that free will is an illusion, I have found an…