Author: Cybernoz
Landmark Admin has issued an update to its investigation of a cyberattack it suffered in May 2024, increasing the number…
For many years, ransomware has been associated with online extortion, causing businesses to become immobilized as they attempt to recover…
Cybercriminals have launched a sophisticated campaign targeting websites hosted on Amazon Web Services (AWS) EC2 instances. This campaign, observed in…
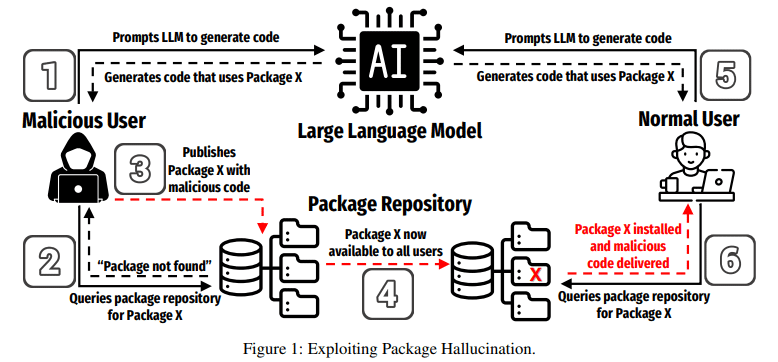
Code-generating large language models (LLMs) have introduced a new security issue into software development: Code package hallucinations. Package hallucinations occur…
How about a web app that filters meritocracy sites (Digg, Reddit, Hacker News) into new feeds based on thresholds of…
China stepped up its allegations of U.S. cyberattacks Tuesday, with local law enforcement saying they were investigating three National Security…
4chan, an infamous online forum, was taken offline earlier today after what appears to be a significant hack and has…
In the rapidly evolving digital landscape of 2025, cybersecurity has reached an inflection point that has prompted an unprecedented reassessment…
OpenAI’s ChatGPT image generator has been exploited to create convincing fake passports in mere minutes, highlighting a significant vulnerability in…
CloudSEK uncovers a sophisticated malware campaign where attackers impersonate PDFCandy.com to distribute the ArechClient2 information stealer. Learn how this scam…
John-Dylan Haynes (Professor at the Bernstein Center for Computational Neuroscience Berlin) shows Marcus Du Sautoy (Professor of Mathematics at the…
Microsoft announced it will begin disabling all ActiveX controls in Windows versions of Microsoft 365 and Office 2024 applications later…