Author: Cybernoz
Amazon Web Services (AWS) has hit out at the UK competition watchdog for presenting “no credible evidence” to support its…
Microsoft says a coding issue is behind a now-resolved Microsoft 365 outage over the weekend that affected Outlook and Exchange…
Cybersecurity firm Silent Push have confirmed recently that North Korean IT workers continue to utilize Astrill VPN services to hide…
The United States has suspended offensive cyber operations against Russia under an order issued by Defense Secretary Pete Hegseth, according…
A new cyberattack campaign discovered by FortiGuard Labs, Fortinet’s threat intelligence and research unit, leverages a combination of social engineering,…
TikTok is the subject of yet another major investigation, reports BBC News. This time around, the UK’s Information Commissioner’s Office…
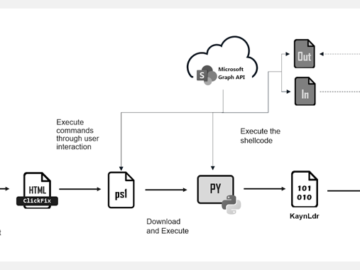
Mar 03, 2025Ravie LakshmananCybercrime / Malware Cybersecurity researchers are calling attention to a new phishing campaign that employs the ClickFix…
A new variant of malware, dubbed “Poco RAT,” has emerged as a potent espionage tool in a campaign targeting Spanish-speaking…
Cybersecurity Ventures predicts that women will represent 30 percent of the global cybersecurity workforce by the end of 2025, increasing to…
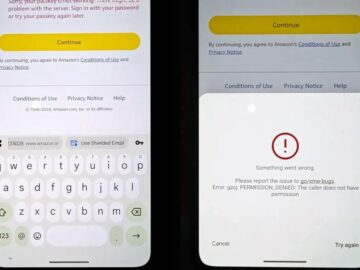
Google is rolling out a new privacy-focused feature called Shielded Email, designed to prevent apps and services from accessing users’ primary…
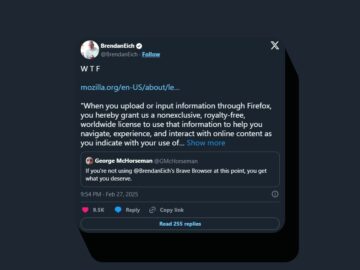
Firefox’s new Terms of Use spark user backlash over data rights. Learn how Mozilla responded to concerns about broad language…
Unit 42 researchers have observed a threat actor group known as JavaGhost exploiting misconfigurations in Amazon Web Services (AWS) environments…