Author: Cybernoz
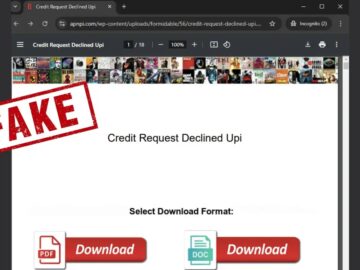
Netskope Threat Labs uncovered a sprawling phishing operation involving 260 domains hosting approximately 5,000 malicious PDF files. These documents, disguised…
In this Help Net Security interview, David Dumont, Partner at Hunton Andrews Kurth, discusses the implications of the EU AI…
A new cybersecurity breach has put over 3.2 million Google Chrome users at risk after hackers hijacked popular browser extensions,…
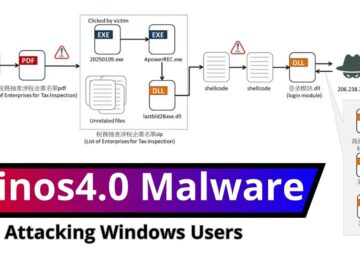
A new wave of cyberattacks leveraging the Winos4.0 malware framework has targeted organizations in Taiwan through malicious PDF attachments disguised…
Here’s a look at the most interesting products from the past month, featuring releases from: 1Password, Armor, BigID, Dynatrace, Fortinet,…
We recently identified a new scam targeting PayPal customers with very convincing ads and pages. Crooks are abusing both Google…
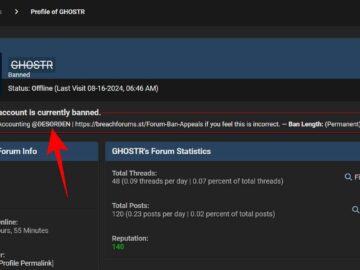
A coordinated effort between law enforcement in Thailand, Singapore, and cybersecurity firm Group-IB has led to the arrest of a…
A new variant of the Vo1d malware botnet has grown to 1,590,299 infected Android TV devices across 226 countries, recruiting…
The Federal Bureau of Investigation said that North Korea was responsible for the theft of approximately US$1.5 billion ($2.4 billion)…
Privacy-focused email provider Tuta (previously Tutanota) and the VPN Trust Initiative (VTI) are raising concerns over proposed laws in France set…
In a concerning development, cybersecurity researchers at Trellix have uncovered a sophisticated malware campaign that exploits a legitimate antivirus driver…
Defence has completed its withdrawal from Global Switch Australia’s data centres a year ahead of its lease expiry, iTnews can…