Author: Cybernoz
Feb 27, 2025The Hacker NewsArtificial Intelligence / Browser Security Organizations are either already adopting GenAI solutions, evaluating strategies for integrating…
A heady mixture of converging trends is likely to cause the volume of disclosed common vulnerabilities and exposures (CVEs) to…
A new wave of phishing attacks impersonating Japanese electronics retail giant Yodobashi Camera has emerged, leveraging urgency and brand trust…
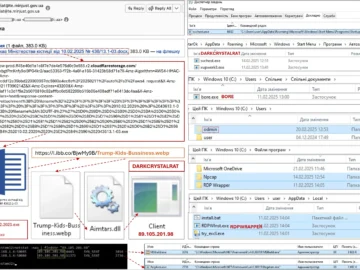
Feb 27, 2025Ravie LakshmananMalware / Network Security The threat actor known as Space Pirates has been linked to a malicious…
Microsoft has fixed a known issue that broke email and calendar drag-and-drop in classic Outlook after installing recent updates on…
The Open Source Security Foundation (OpenSSF) has launched the Open Source Project Security Baseline (OSPS Baseline), a tiered framework designed…
Recent revelations about Google’s SafetyCore app have ignited a firestorm of privacy debates, echoing Apple’s recent controversy over photo scanning….
The cybersecurity and compliance landscape in 2025 is more complex and challenging than ever before. The rapid evolution of cyber…
Cybersecurity researchers at Kaspersky’s Securelist have found a cyber espionage group known as Angry Likho APT (also referred to as Sticky Werewolf by some…
The cybersecurity industry is experiencing unprecedented growth, fueled by increasing cyber threats, the expansion of cloud computing, and the adoption of…
Cisco Systems has issued a critical security advisory addressing a command injection vulnerability in its Nexus 3000 and 9000 Series…
CERT-UA, the Governmental Computer Emergency Response Team of Ukraine, reported a resurgence of the notorious criminal group UAC-0173. This group,…