Author: Cybernoz
Sometimes the updates we install to keep our devices safe do a little bit more than we might suspect at…
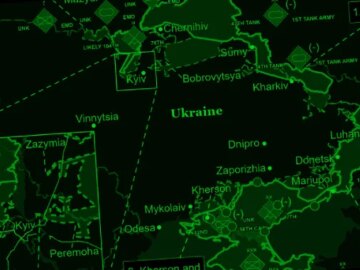
Feb 26, 2025Ravie LakshmananNetwork Security / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) on Tuesday warned of…
The failure of Scottish policing bodies to record the ethnicity of arrested people it takes DNA samples from means there…
Dive Brief: Approximately 2,850 IP addresses are vulnerable to CVE-2025-22467, a critical stack buffer-overflow vulnerability that affects Ivanti Connect Secure…
The immensely popular memecoin generator Pump.fun had its X account hacked to promote a fake “PUMP” token cryptocurrency scam. Pump.fun…
A critical set of 20 security vulnerabilities in GRUB2, the widely used bootloader for Linux systems, has been revealed, exposing…
A data breach at DISA Global Solutions, a firm providing background checks, and drugs and alcohol testing services, exposed the…
Data breaches have become increasingly common in recent years, yet the level of concern surrounding these information leaks has grown…
For many CISOs, compliance can feel like a necessary evil and a false sense of security. While frameworks like ISO…
Last week it was reported that a lawsuit has been initiated against gaming giant Roblox and leading messaging platform Discord. The…
Feb 26, 2025The Hacker NewsIdentity Protection / Password Security Passwords are rarely appreciated until a security breach occurs; suffice to…
In this podcast we talk with Cody David, solutions architect with Syniti, which is part of Capgemini, about the importance…