Author: Cybernoz
Kaspersky’s Securelist exposes the GitVenom campaign involving fake GitHub repositories to distribute malware. Targeting developers with seemingly legitimate open-source projects,…
Weak passwords, as various studies have shown, can be cracked in a second, but now AI can crack even stronger…
DISA Global Solutions, a leading US background screening and drug and alcohol testing firm, has suffered a data breach impacting…
The LightSpy advanced persistent threat (APT) group has significantly upgraded its surveillance capabilities with a 100+ command framework targeting Android,…
The Socket Research Team has uncovered a malicious npm package@ton-wallet/create designed to steal sensitive cryptocurrency wallet keys from developers and…
Email encryption is an essential protection for modern businesses. The software market has adapted to this need, so leaders have…
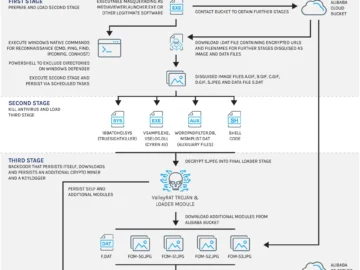
Silver Fox, a China-based threat actor that may or may not be backed by the Chinese government, has been delivering…
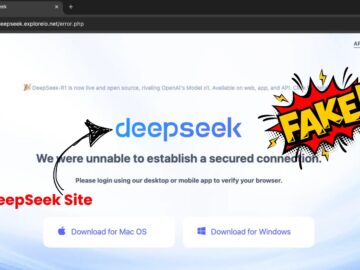
Cybersecurity researchers uncovered a sophisticated macOS malware campaign distributing the Poseidon Stealer through a counterfeit DeepSeek AI platform website. This…
Enacted in 1996, the Health Insurance Portability and Accountability Act (HIPAA) has been the regulatory standard for U.S. healthcare providers,…
Dive Brief: GreyNoise researchers observed active exploitation of two Cisco vulnerabilities, CVE-2018-0171 and CVE-2023-20198, which reportedly have been used in recent…
INE, the leading provider of networking and cybersecurity training and certifications, today announced its recognition as an enterprise and small…
Employment screening company DISA Global Solutions has filed a data breach notification after a cyber incident on their network. DISA…