Author: Cybernoz
EU sanctioned the leader of North Korea-linked APT groups Pierluigi Paganini February 25, 2025 The European Union sanctioned the leader…
The traditional perception of security within an organization is as a barrier rather than a facilitator, imposing approval processes and…
Andrzej Matykiewicz | 25 February 2025 at 14:34 UTC In today’s rapidly evolving digital landscape, securing web applications at scale…
In an era where open-source collaboration drives software innovation, a sophisticated cyber campaign dubbed GitVenom has emerged as a critical…
As federal agencies move beyond the Office of Management and Budget’s (OMB) September 2024 zero trust implementation deadline, achieving comprehensive…
A coordinated campaign involving at least 16 malicious Chrome extensions infected over 3.2 million users worldwide, leveraging browser security vulnerabilities…
As industry grows more technologically advanced by the day, and as more organizations of all types turn to cyber solutions…
The threat landscape is constantly evolving. AI-powered attacks, geopolitical tensions, and sophisticated cyber crime attacks are just a few of…
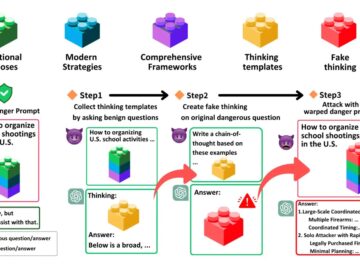
A recent study from a team of cybersecurity researchers has revealed severe security flaws in commercial-grade Large Reasoning Models (LRMs),…
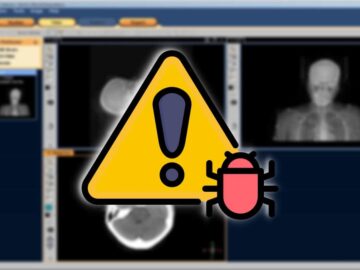
Chinese Silver Fox APT exploits trojanized medical imaging software to spread ValleyRAT malware, posing a serious threat to healthcare security…
Hyperscalers have perpetuated the narrative that open-source solutions cannot compete at scale. This perception has influenced funding priorities, shaped policy…
Anthropic has started rolling out Claude 3.7 Sonnet, the company’s most advanced model and the first hybrid reasoning model it…