Author: Cybernoz
A newly disclosed vulnerability in the GRUB2 bootloader’s read command (CVE-2025-0690) has raised concerns about potential Secure Boot bypasses and…
DeepSeek has taken the AI world by storm, surpassing ChatGPT as the most downloaded smartphone app and gaining rapid adoption…
Feb 25, 2025Ravie LakshmananGaming / Threat Intelligence Cybersecurity researchers are calling attention to an ongoing campaign that’s targeting gamers and…
In a transformative move for smartphone longevity, Qualcomm Technologies, Inc., and Google have announced a collaboration to enable eight years…
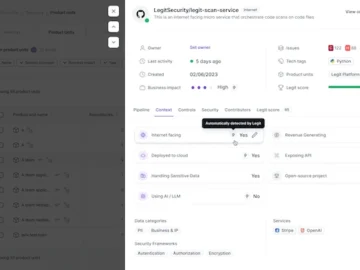
By providing full context around both the application and the development environment, Legit’s ASPM platform empowers CISOs and their team…
Feb 25, 2025Ravie LakshmananWindows Security / Vulnerability A large-scale malware campaign has been found leveraging a vulnerable Windows driver associated…
The Council of the European Union took decisive action to impose a new set of sanctions on Russia, with the…
“Regrettably, I found no available source online to know more about this organization except for those registrations,” wrote the complainant….
The first quarter of 2025 has been a battlefield in the world of cybersecurity. Cybercriminals continued launching aggressive new campaigns…
As we mark the third anniversary of the Russian invasion of Ukraine in February 2022, it is essential to reflect…
U.S. CISA adds Adobe ColdFusion and Oracle Agile PLM flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 25, 2025…
A hacker claims to have stolen thousands of internal documents with user records and employee data after breaching the systems…