Author: Cybernoz
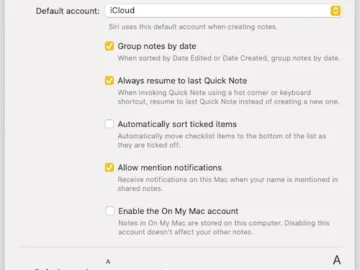
Apple allows you to lock your notes using your iPhone passcode or a separate password, ensuring your private information stays…
A cluster of four critical vulnerabilities in Ivanti Endpoint Manager (EPM) has entered a dangerous new phase with the public…
A GitHub repository titled Windows-WiFi-Password-Stealer has surfaced, raising concerns among cybersecurity professionals. This repository, hosted by the user, provides a…
Here’s a look at the most interesting products from the past week, featuring releases from 1Password, Fortinet, Pangea, Privacera, and…
Google’s Project Zero and Mandiant cybersecurity teams have jointly published a proof-of-concept (PoC) exploit for a high-severity command injection vulnerability…
RedTeamPentesting has unveiled a new tool, keycred, which offers a robust solution for managing KeyCredentialLinks in Active Directory (AD) environments….
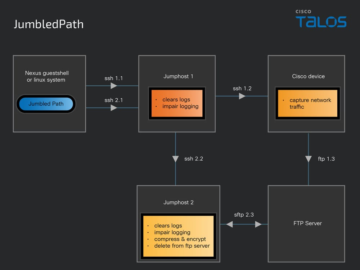
Salt Typhoon used custom malware JumbledPath to spy U.S. telecom providers Pierluigi Paganini February 20, 2025 China-linked cyber espionage group…
Learn how to sue companies under GDPR for data misuse. Understand your rights, file complaints, and claim compensation for privacy…
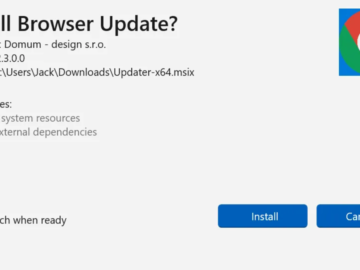
Cybersecurity researchers have uncovered a sophisticated malware campaign orchestrated by the threat actor group SmartApeSG, also known as ZPHP or…
An unknown leaker has released what they claim to be an archive of internal Matrix chat logs belonging to the…
A recent phishing campaign conducted by cybersecurity firm Hackmosphere has revealed alarming vulnerabilities among top decision-makers, including CEOs and CTOs….
Security researchers at Apiiro have released two free, open-source tools designed to detect and block malicious code before they are…