Author: Cybernoz
by Andrea Poteet-Bell, Editor Author Content Writer, Sunshine Behavioral Health Identity theft is constantly in the news. According to a…
Enhancing your security and privacy on iOS 18 involves configuring various settings to control access to your personal data and…
CaixaBank will invest in programmes to make more use of artificial intelligence (AI), as part of a multibillion-euro business plan…
For years, defensive security strategies have focused on three core areas: network, endpoint, and email. Meanwhile, the browser, where most…
Russian state-aligned threat actors have intensified their efforts to compromise Signal Messenger accounts, targeting individuals of strategic interest, according to…
Understanding Data Privacy by Gergo Varga, Senior Content Manager, SEON Today, we are living in a world where data is…
Nearly six months ago, the Western media began to highlight growing concerns about potential Chinese interference in critical U.S. infrastructure….
Palo Alto Networks warns that a file read vulnerability (CVE-2025-0111) is now being chained in attacks with two other flaws…
Authored by the Publisher of Cyber Security Magazine Deep fake videos and audios – including phone calls from cyber criminals,…
Cary, North Carolina, February 19th, 2025, CyberNewsWire 2025 marks a time of unprecedented volatility in the technology job market. On…
Cary, North Carolina, February 19th, 2025, CyberNewsWire 2025 marks a time of unprecedented volatility in the technology job market. On…
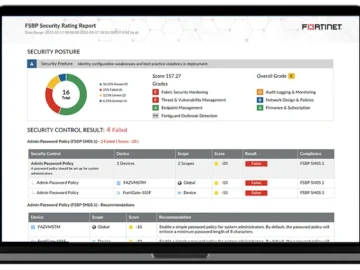
Fortinet announced significant enhancements to FortiAnalyzer, reinforcing its role in driving faster, smarter security operations (SecOps)—all from a single, turnkey…