Author: Cybernoz
Data loss is becoming a bigger danger for businesses, both financially and numerically. According to an IBM report, the average data…
Feb 18, 2025Ravie LakshmananThreat Intelligence / Malware Cybersecurity researchers are alerting to a new campaign that leverages web injects to…
A newly created public-private partnership looks set to oversee the creation of the world’s largest artificial intelligence (AI) datacentre in…
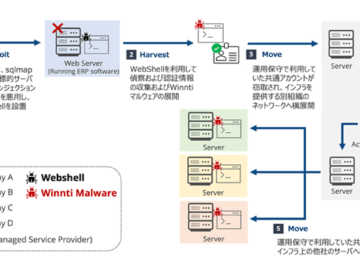
Feb 18, 2025Ravie LakshmananMalware / Network Security The China-linked threat actor known as Winnti has been attributed to a new…
The CrowdStrike incident in 2024 hit the UK like a hurricane. As it swept across the country, it ground flights…
Newspaper publishing giant Lee Enterprises has confirmed that a ransomware attack is behind ongoing disruptions impacting the group’s operations for…
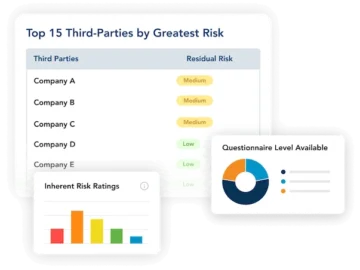
ProcessUnity announced the next generation of the Global Risk Exchange. This platform transforms the third-party assessment process, reducing friction for…
Feb 18, 2025Ravie LakshmananVulnerability / Network Security Juniper Networks has released security updates to address a critical security flaw impacting…
Thank you for joining! Access your Pro+ Content below. 18 February 2025 AI Action Summit calls for a rethink of…
Feb 18, 2025The Hacker NewsArtificial Intelligence / Cyber Defense Is AI really reshaping the cyber threat landscape, or is the…
Meta has announced its plan for a subsea cable that will span the globe, connecting emerging economies such as India,…
Researchers from Trend Micro’s Threat Hunting team have uncovered a sophisticated cyberattack campaign by the advanced persistent threat (APT) group…