Author: Cybernoz
GreyNoise has noted a sharp escalation in hacking attempts targeting TVT NVMS9000 Digital Video Recorders (DVRs). The surge in malicious…
Apr 09, 2025The Hacker NewsSecrets Management / DevOps GitGuardian’s State of Secrets Sprawl report for 2025 reveals the alarming scale…
Victoria Police is deploying an app to its mobile device fleet that digitises the issuing of roadside infringement notices. The…
Ever wonder what mail servers people run? I found myself wondering what the top universities used, so I wrote a…
Ransomware attacks have continued their relentless assault on organizations worldwide, with a focus on data exfiltration and subsequent blackmail through…
Luxembourg, Luxembourg, April 9th, 2025, CyberNewsWire Gcore, the global edge AI, cloud, network, and security solutions provider, has launched Super…
A critical RCE vulnerability (CVE-2025-30406) affecting the Gladinet CentreStack file-sharing/remote access platform has been added to CISA’s Known Exploited Vulnerabilities…
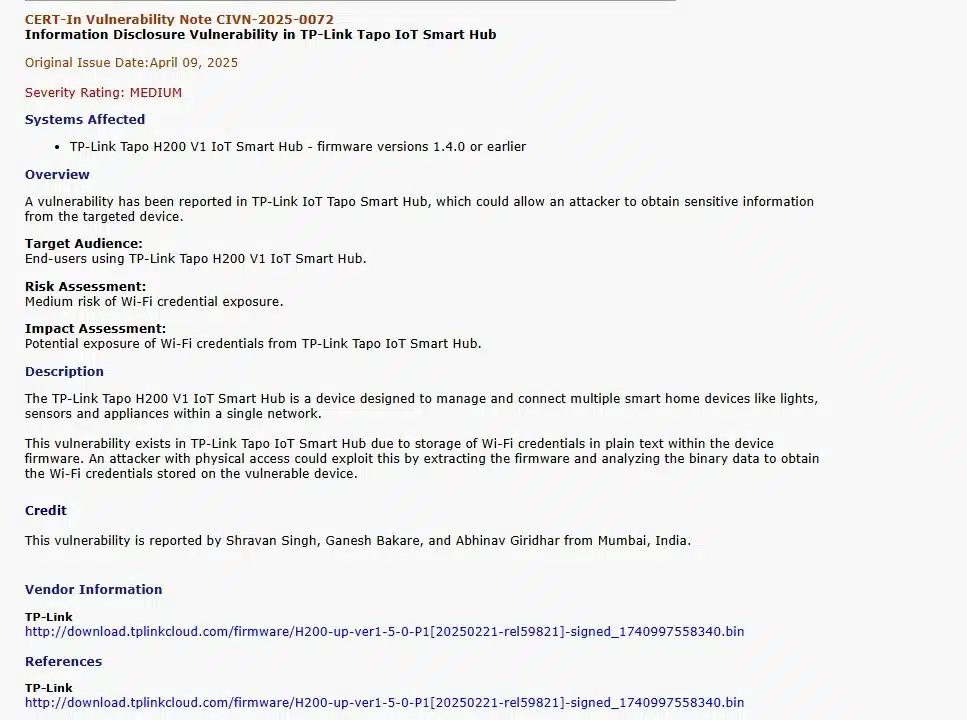
A new vulnerability has been identified in the TP-Link Tapo H200 V1 IoT Smart Hub that could allow attackers to…
The religious love to claim Einstein as their own. They do so because the misinterpret his remarks referring to nature…
Microsoft has uncovered a sophisticated ransomware campaign exploiting a zero-day vulnerability in the Windows Common Log File System (CLFS), tracked…
Apr 09, 2025Ravie LakshmananApplication Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical…
At RSA this year I caught a talk by a Google executive that discussed what makes Google’s Information Security team…