Author: Cybernoz
Saudi Arabia is spending big on IT, and on artificial intelligence (AI) in particular, in an effort to diversify from…
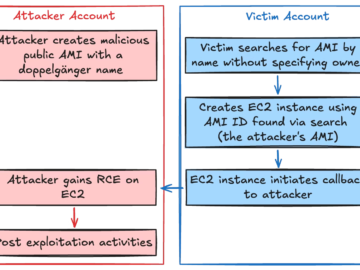
whoAMI attack could allow remote code execution within AWS account Pierluigi Paganini February 17, 2025 Researchers warn that the whoAMI…
Security researchers at Volexity have uncovered multiple Russian threat actors conducting sophisticated social engineering and spear-phishing campaigns targeting Microsoft 365…
Organisations should build their own generative artificial intelligence-based (GenAI-based) on retrieval augmented generation (RAG) with open sources products such as…
Google is working to enhance the security of its mobile operating system, focusing on preventing scammers from exploiting certain phone…
The Indian Post Office portal was found vulnerable to an Insecure Direct Object Reference (IDOR) attack, exposing sensitive Know Your…
Today’s data landscape presents unprecedented challenges for organisations, due to the need for businesses to process thousands of documents in…
A sophisticated cyber threat has emerged in recent weeks, targeting unsuspecting users with fake Outlook troubleshooting calls. These calls, designed…
February 14, 2025 – A cybercriminal stole a reported 12 million data records on Zacks’ customers and clients. February 13,…
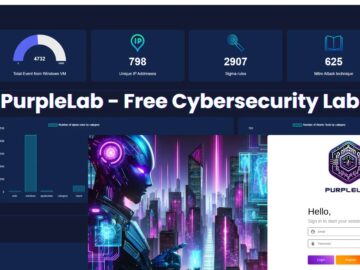
In a significant step forward for cybersecurity professionals, PurpleLab offers an innovative open-source cybersecurity lab for creating and testing detection…
Threat actors have been utilizing a modified version of the SharpHide tool to create hidden registry values, significantly complicating detection…
Samsung has consistently been at the forefront of technological innovation, and its latest advancement comes in the form of enhanced…