Author: Cybernoz
Cyber threats have evolved significantly in recent years, with malicious actors employing sophisticated tactics to compromise user systems. One such…
North Korean IT workers have been infiltrating international companies by securing remote positions under false identities. This tactic not only…
The notorious Lazarus Group in a recent escalation of cyber threats linked to North Korea, has unveiled a sophisticated new…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Microsoft fixes two actively exploited…
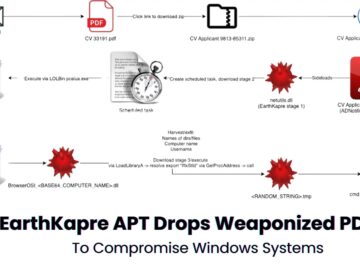
A highly sophisticated cyber espionage group known as EarthKapre, also referred to as RedCurl, has been identified targeting private-sector organizations,…
Job seekers have become the target of a sophisticated ransomware campaign in a recent cybersecurity threat, and this campaign dubbed…
The notorious Lazarus Group, a North Korean Advanced Persistent Threat (APT) group, has been linked to a sophisticated campaign targeting…
A website launched by Elon Musk’s Department of Government Efficiency (DOGE) has been found to have a significant security vulnerability,…
A recently discovered Python script has been flagged as a potential cybersecurity threat due to its use of a clever…
Researchers have identified a new backdoor malware, written in Go programming language, that leverages Telegram as its command-and-control (C2) channel….
A critical authentication bypass vulnerability in SonicWall firewalls, tracked as CVE-2024-53704, is now being actively exploited in the wild, cybersecurity…
I wrote recently about the difference between Functional and Technical AGI. I argued that Technical AGI is the real deal…